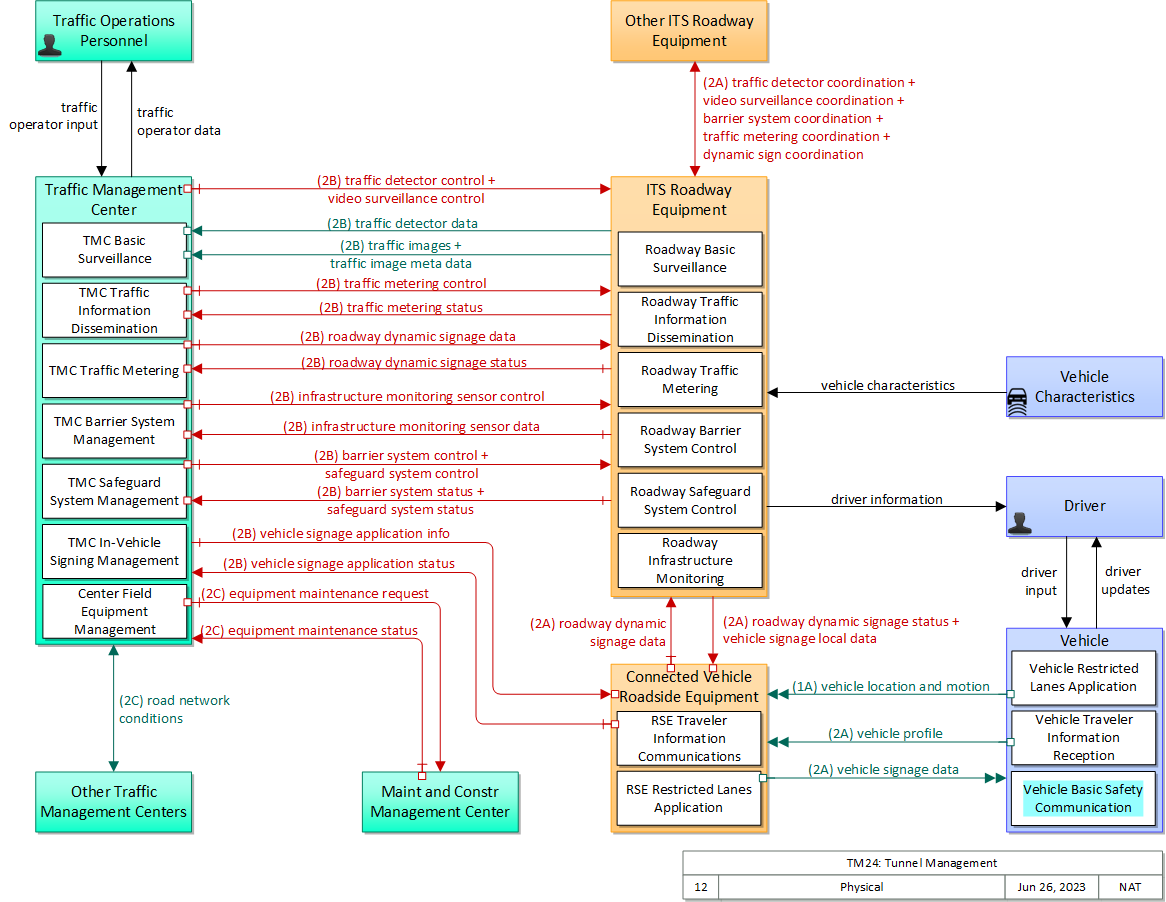
TM24: Tunnel Management
This service package provides central monitoring and control, communications, and field equipment that supports traffic management in tunnels. It specifically includes additional features that support operational safety in tunnels including air quality sensors, infrastructure integrity sensors, and security and surveillance equipment that monitor tunnel operations and signals, dynamic message signs, lighting, and tunnel-specific field equipment like exhaust fans to support safe tunnel traffic operations.
![]() Origin: European Union
Origin: European Union
Relevant Regions: Australia, Canada, European Union, and United States
- Enterprise
- Functional
- Physical
- Goals and Objectives
- Needs and Requirements
- Sources
- Security
- Standards
- System Requirements
Enterprise
Development Stage Roles and Relationships
Installation Stage Roles and Relationships
Operations and Maintenance Stage Roles and Relationships
(hide)
| Source | Destination | Role/Relationship |
|---|---|---|
| Connected Vehicle Roadside Equipment Maintainer | Connected Vehicle Roadside Equipment | Maintains |
| Connected Vehicle Roadside Equipment Manager | Connected Vehicle Roadside Equipment | Manages |
| Connected Vehicle Roadside Equipment Owner | Connected Vehicle Roadside Equipment Maintainer | System Maintenance Agreement |
| Connected Vehicle Roadside Equipment Owner | Connected Vehicle Roadside Equipment Manager | Operations Agreement |
| Connected Vehicle Roadside Equipment Owner | Driver | Application Usage Agreement |
| Connected Vehicle Roadside Equipment Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Connected Vehicle Roadside Equipment Owner | ITS Roadway Equipment Owner | Information Exchange and Action Agreement |
| Connected Vehicle Roadside Equipment Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Connected Vehicle Roadside Equipment Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| Connected Vehicle Roadside Equipment Owner | Traffic Management Center Owner | Information Exchange and Action Agreement |
| Connected Vehicle Roadside Equipment Owner | Traffic Management Center User | Service Usage Agreement |
| Connected Vehicle Roadside Equipment Owner | Traffic Operations Personnel | Application Usage Agreement |
| Connected Vehicle Roadside Equipment Owner | Vehicle Maintainer | Maintenance Data Exchange Agreement |
| Connected Vehicle Roadside Equipment Owner | Vehicle Owner | Information Exchange and Action Agreement |
| Connected Vehicle Roadside Equipment Owner | Vehicle User | Service Usage Agreement |
| Connected Vehicle Roadside Equipment Supplier | Connected Vehicle Roadside Equipment Owner | Warranty |
| Driver | Vehicle | Operates |
| ITS Roadway Equipment Maintainer | ITS Roadway Equipment | Maintains |
| ITS Roadway Equipment Manager | ITS Roadway Equipment | Manages |
| ITS Roadway Equipment Owner | Connected Vehicle Roadside Equipment Maintainer | Maintenance Data Exchange Agreement |
| ITS Roadway Equipment Owner | Connected Vehicle Roadside Equipment Owner | Information Exchange and Action Agreement |
| ITS Roadway Equipment Owner | Connected Vehicle Roadside Equipment User | Service Usage Agreement |
| ITS Roadway Equipment Owner | ITS Roadway Equipment Maintainer | System Maintenance Agreement |
| ITS Roadway Equipment Owner | ITS Roadway Equipment Manager | Operations Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment Owner | Information Exchange and Action Agreement |
| ITS Roadway Equipment Owner | Other ITS Roadway Equipment User | Service Usage Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center Owner | Information Exchange and Action Agreement |
| ITS Roadway Equipment Owner | Traffic Management Center User | Service Usage Agreement |
| ITS Roadway Equipment Owner | Traffic Operations Personnel | Application Usage Agreement |
| ITS Roadway Equipment Supplier | ITS Roadway Equipment Owner | Warranty |
| Maint and Constr Management Center Maintainer | Maint and Constr Management Center | Maintains |
| Maint and Constr Management Center Manager | Maint and Constr Management Center | Manages |
| Maint and Constr Management Center Owner | Maint and Constr Management Center Maintainer | System Maintenance Agreement |
| Maint and Constr Management Center Owner | Maint and Constr Management Center Manager | Operations Agreement |
| Maint and Constr Management Center Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| Maint and Constr Management Center Owner | Traffic Management Center Owner | Information Exchange Agreement |
| Maint and Constr Management Center Owner | Traffic Management Center User | Service Usage Agreement |
| Maint and Constr Management Center Owner | Traffic Operations Personnel | Application Usage Agreement |
| Maint and Constr Management Center Supplier | Maint and Constr Management Center Owner | Warranty |
| Other ITS Roadway Equipment Maintainer | Other ITS Roadway Equipment | Maintains |
| Other ITS Roadway Equipment Manager | Other ITS Roadway Equipment | Manages |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment Owner | Information Exchange and Action Agreement |
| Other ITS Roadway Equipment Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Other ITS Roadway Equipment Owner | Other ITS Roadway Equipment Maintainer | System Maintenance Agreement |
| Other ITS Roadway Equipment Owner | Other ITS Roadway Equipment Manager | Operations Agreement |
| Other ITS Roadway Equipment Supplier | Other ITS Roadway Equipment Owner | Warranty |
| Other Traffic Management Centers Maintainer | Other Traffic Management Centers | Maintains |
| Other Traffic Management Centers Manager | Other Traffic Management Centers | Manages |
| Other Traffic Management Centers Owner | Other Traffic Management Centers Maintainer | System Maintenance Agreement |
| Other Traffic Management Centers Owner | Other Traffic Management Centers Manager | Operations Agreement |
| Other Traffic Management Centers Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| Other Traffic Management Centers Owner | Traffic Management Center Owner | Information Exchange Agreement |
| Other Traffic Management Centers Owner | Traffic Management Center User | Service Usage Agreement |
| Other Traffic Management Centers Owner | Traffic Operations Personnel | Application Usage Agreement |
| Other Traffic Management Centers Supplier | Other Traffic Management Centers Owner | Warranty |
| Traffic Management Center Maintainer | Traffic Management Center | Maintains |
| Traffic Management Center Manager | Traffic Management Center | Manages |
| Traffic Management Center Manager | Traffic Operations Personnel | System Usage Agreement |
| Traffic Management Center Owner | Connected Vehicle Roadside Equipment Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | Connected Vehicle Roadside Equipment Owner | Information Provision Agreement |
| Traffic Management Center Owner | Connected Vehicle Roadside Equipment User | Service Usage Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment Owner | Information Provision Agreement |
| Traffic Management Center Owner | ITS Roadway Equipment User | Service Usage Agreement |
| Traffic Management Center Owner | Maint and Constr Management Center Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | Maint and Constr Management Center Owner | Information Exchange Agreement |
| Traffic Management Center Owner | Maint and Constr Management Center User | Service Usage Agreement |
| Traffic Management Center Owner | Other Traffic Management Centers Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | Other Traffic Management Centers Owner | Information Exchange Agreement |
| Traffic Management Center Owner | Other Traffic Management Centers User | Service Usage Agreement |
| Traffic Management Center Owner | Traffic Management Center Maintainer | System Maintenance Agreement |
| Traffic Management Center Owner | Traffic Management Center Manager | Operations Agreement |
| Traffic Management Center Supplier | Traffic Management Center Owner | Warranty |
| Traffic Operations Personnel | Traffic Management Center | Operates |
| Vehicle Characteristics Maintainer | Vehicle Characteristics | Maintains |
| Vehicle Characteristics Manager | Vehicle Characteristics | Manages |
| Vehicle Characteristics Owner | Vehicle Characteristics Maintainer | System Maintenance Agreement |
| Vehicle Characteristics Owner | Vehicle Characteristics Manager | Operations Agreement |
| Vehicle Characteristics Supplier | Vehicle Characteristics Owner | Warranty |
| Vehicle Maintainer | Vehicle | Maintains |
| Vehicle Manager | Driver | System Usage Agreement |
| Vehicle Manager | Vehicle | Manages |
| Vehicle Owner | Connected Vehicle Roadside Equipment Maintainer | Maintenance Data Exchange Agreement |
| Vehicle Owner | Connected Vehicle Roadside Equipment Owner | Expectation of Data Provision |
| Vehicle Owner | Connected Vehicle Roadside Equipment User | Service Usage Agreement |
| Vehicle Owner | Vehicle Maintainer | System Maintenance Agreement |
| Vehicle Owner | Vehicle Manager | Operations Agreement |
| Vehicle Supplier | Vehicle Owner | Warranty |
Functional
This service package includes the following Functional View PSpecs:
Physical
The physical diagram can be viewed in SVG or PNG format and the current format is SVG.SVG Diagram
PNG Diagram
Includes Physical Objects:
| Physical Object | Class | Description |
|---|---|---|
| Connected Vehicle Roadside Equipment | Field | 'Connected Vehicle Roadside Equipment' (CV RSE) represents the Connected Vehicle roadside devices (i.e., Roadside Units (RSUs)) equipped with short range wireless (SRW) communications technology, as well as any other supporting equipment that leverage the RSU and are not described by other objects (e.g., a local roadside processor). CVRSE are used to send messages to, and receive messages from, nearby vehicles and personal devices equipped with compatible communications technology. Communications with adjacent field equipment and back office centers that monitor and control the RSE are also supported. This device operates from a fixed position and may be permanently deployed or a portable device that is located temporarily in the vicinity of a traffic incident, road construction, or a special event. It includes a processor, data storage, and communications capabilities that support secure communications with passing vehicles, other field equipment, and centers. |
| Driver | Vehicle | The 'Driver' represents the person that operates a vehicle on the roadway. Included are operators of private, transit, commercial, and emergency vehicles where the interactions are not particular to the type of vehicle (e.g., interactions supporting vehicle safety applications). The Driver originates driver requests and receives driver information that reflects the interactions which might be useful to all drivers, regardless of vehicle classification. Information and interactions which are unique to drivers of a specific vehicle type (e.g., fleet interactions with transit, commercial, or emergency vehicle drivers) are covered by separate objects. |
| ITS Roadway Equipment | Field | 'ITS Roadway Equipment' represents the ITS equipment that is distributed on and along the roadway that monitors and controls traffic and monitors and manages the roadway. This physical object includes traffic detectors, environmental sensors, traffic signals, highway advisory radios, dynamic message signs, CCTV cameras and video image processing systems, grade crossing warning systems, and ramp metering systems. Lane management systems and barrier systems that control access to transportation infrastructure such as roadways, bridges and tunnels are also included. This object also provides environmental monitoring including sensors that measure road conditions, surface weather, and vehicle emissions. Work zone systems including work zone surveillance, traffic control, driver warning, and work crew safety systems are also included. |
| Maint and Constr Management Center | Center | The 'Maint and Constr Management Center' monitors and manages roadway infrastructure construction and maintenance activities. Representing both public agencies and private contractors that provide these functions, this physical object manages fleets of maintenance, construction, or special service vehicles (e.g., snow and ice control equipment). The physical object receives a wide range of status information from these vehicles and performs vehicle dispatch, routing, and resource management for the vehicle fleets and associated equipment. The physical object participates in incident response by deploying maintenance and construction resources to an incident scene, in coordination with other center physical objects. The physical object manages equipment at the roadside, including environmental sensors and automated systems that monitor and mitigate adverse road and surface weather conditions. It manages the repair and maintenance of both non-ITS and ITS equipment including the traffic controllers, detectors, dynamic message signs, signals, and other equipment associated with the roadway infrastructure. Weather information is collected and fused with other data sources and used to support advanced decision support systems. The physical object remotely monitors and manages ITS capabilities in work zones, gathering, storing, and disseminating work zone information to other systems. It manages traffic in the vicinity of the work zone and advises drivers of work zone status (either directly at the roadside or through an interface with the Transportation Information Center or Traffic Management Center physical objects.) Construction and maintenance activities are tracked and coordinated with other systems, improving the quality and accuracy of information available regarding closures and other roadway construction and maintenance activities. |
| Other ITS Roadway Equipment | Field | Representing another set of ITS Roadway Equipment, 'Other ITS Roadway Equipment' supports 'field device' to 'field device' communication and coordination, and provides a source and destination for information that may be exchanged between ITS Roadway Equipment. The interface enables direct coordination between field equipment. Examples include the direct interface between sensors and other roadway devices (e.g., Dynamic Message Signs) and the direct interface between roadway devices (e.g., between a Signal System Master and Signal System Local equipment) or a connection between an arterial signal system master and a ramp meter controller. |
| Other Traffic Management Centers | Center | Representing another Traffic Management Center, 'Other Traffic Management Centers' is intended to provide a source and destination for information exchange between peer (e.g. inter-regional) traffic management functions. It enables traffic management activities to be coordinated across different jurisdictional areas. |
| Traffic Management Center | Center | The 'Traffic Management Center' monitors and controls traffic and the road network. It represents centers that manage a broad range of transportation facilities including freeway systems, rural and suburban highway systems, and urban and suburban traffic control systems. It communicates with ITS Roadway Equipment and Connected Vehicle Roadside Equipment (RSE) to monitor and manage traffic flow and monitor the condition of the roadway, surrounding environmental conditions, and field equipment status. It manages traffic and transportation resources to support allied agencies in responding to, and recovering from, incidents ranging from minor traffic incidents through major disasters. |
| Traffic Operations Personnel | Center | 'Traffic Operations Personnel' represents the people that operate a traffic management center. These personnel interact with traffic control systems, traffic surveillance systems, incident management systems, work zone management systems, and travel demand management systems. They provide operator data and command inputs to direct system operations to varying degrees depending on the type of system and the deployment scenario. |
| Vehicle | Vehicle | This 'Vehicle' physical object is used to model core capabilities that are common to more than one type of Vehicle. It provides the vehicle-based general sensory, processing, storage, and communications functions that support efficient, safe, and convenient travel. Many of these capabilities (e.g., see the Vehicle Safety service packages) apply to all vehicle types including personal vehicles, commercial vehicles, emergency vehicles, transit vehicles, and maintenance vehicles. From this perspective, the Vehicle includes the common interfaces and functions that apply to all motorized vehicles. The radio(s) supporting V2V and V2I communications are a key component of the Vehicle. Both one-way and two-way communications options support a spectrum of information services from basic broadcast to advanced personalized information services. Advanced sensors, processors, enhanced driver interfaces, and actuators complement the driver information services so that, in addition to making informed mode and route selections, the driver travels these routes in a safer and more consistent manner. This physical object supports all six levels of driving automation as defined in SAE J3016. Initial collision avoidance functions provide 'vigilant co-pilot' driver warning capabilities. More advanced functions assume limited control of the vehicle to maintain lane position and safe headways. In the most advanced implementations, this Physical Object supports full automation of all aspects of the driving task, aided by communications with other vehicles in the vicinity and in coordination with supporting infrastructure subsystems. |
| Vehicle Characteristics | Vehicle | 'Vehicle Characteristics' represents the external view of individual vehicles of any class from cars and light trucks up to large commercial vehicles and down to micromobility vehicles (MMVs). It includes vehicle physical characteristics such as height, width, length, weight, and other properties (e.g., magnetic properties, number of axles) of individual vehicles that can be sensed and measured or classified. This physical object represents the physical properties of vehicles that can be sensed by vehicle-based or infrastructure-based sensors to support vehicle automation and traffic sensor systems. The analog properties provided by this terminator represent the sensor inputs that are used to detect and assess vehicle(s) within the sensor's range to support safe AV operation and/or responsive and safe traffic management. |
Includes Functional Objects:
| Functional Object | Description | Physical Object |
|---|---|---|
| Center Field Equipment Management | 'Center Field Equipment Management' is the back office application that supports monitoring and maintenance of field equipment. It monitors the performance and configuration of the field equipment. This includes management of the infrastructure configuration as well as detection, isolation, and correction of field equipment problems. The application also includes monitoring of performance of the field equipment, including communications links. | Center |
| Roadway Barrier System Control | 'Roadway Barrier System Control' includes the field equipment that controls barrier systems used to control access to transportation facilities and infrastructure. Barrier systems include automatic or remotely controlled gates, barriers and other access control systems. | ITS Roadway Equipment |
| Roadway Basic Surveillance | 'Roadway Basic Surveillance' monitors traffic conditions using fixed equipment such as loop detectors and CCTV cameras. | ITS Roadway Equipment |
| Roadway Infrastructure Monitoring | 'Roadway Infrastructure Monitoring' monitors the condition of pavement, bridges, tunnels, associated hardware, and other transportation-related infrastructure (e.g., culverts). It includes sensors that monitor the infrastructure and the communications necessary to report this data to a center or vehicle-based maintenance system. | ITS Roadway Equipment |
| Roadway Safeguard System Control | 'Roadway Safeguard System Control' includes field equipment that controls safeguard systems for transportation facilities and infrastructure. Safeguard systems include blast shields, exhaust systems and other automatic or remotely controlled systems intended to mitigate the impact of an incident. | ITS Roadway Equipment |
| Roadway Traffic Information Dissemination | 'Roadway Traffic Information Dissemination' includes field elements that provide information to drivers, including dynamic message signs and highway advisory radios. | ITS Roadway Equipment |
| Roadway Traffic Metering | 'Roadway Traffic Metering' includes the field equipment used to meter traffic on ramps, through interchanges, and on the mainline roadway. The equipment includes dynamic messages signs to provide guidance and information to drivers at and approaching a meter, including information for any special bypass lanes. | ITS Roadway Equipment |
| RSE Restricted Lanes Application | The 'RSE Restricted Lanes Application' uses short range communications to monitor and manage dynamic and static restricted lanes. It collects vehicle profile information from vehicles entering the lanes and monitors vehicles within the lanes, providing aggregate data to the back office center. It provides lane restriction information and signage data to the vehicles and optionally identifies vehicles that violate the current lane restrictions. These functions are performed based on operating parameters provided by the back office managing center(s). | Connected Vehicle Roadside Equipment |
| RSE Traveler Information Communications | 'RSE Traveler Information Communications' includes field elements that distribute information to vehicles for in-vehicle display. The information may be provided by a center (e.g., variable information on traffic and road conditions in the vicinity of the field equipment) or it may be determined and output locally (e.g., static sign information and signal phase and timing information). This includes the interface to the center or field equipment that controls the information distribution and the short range communications equipment that provides information to passing vehicles. | Connected Vehicle Roadside Equipment |
| TMC Barrier System Management | 'TMC Barrier System Management' remotely monitors and controls barrier systems for transportation facilities and infrastructure under control of center personnel. Barrier systems include automatic or remotely controlled gates, barriers and other access control systems. It also provides an interface to other centers to allow monitoring and control of the barriers from other centers (e.g., public safety or emergency operations centers). | Traffic Management Center |
| TMC Basic Surveillance | 'TMC Basic Surveillance' remotely monitors and controls traffic sensor systems and surveillance (e.g., CCTV) equipment, and collects, processes and stores the collected traffic data. Current traffic information and other real-time transportation information is also collected from other centers. The collected information is provided to traffic operations personnel and made available to other centers. | Traffic Management Center |
| TMC In-Vehicle Signing Management | 'TMC In-Vehicle Signing Management' controls and monitors RSEs that support in-vehicle signing. Sign information that may include static regulatory, service, and directional sign information as well as variable information such as traffic and road conditions can be provided to the RSE, which uses short range communications to send the information to in-vehicle equipment. Information that is currently being communicated to passing vehicles and the operational status of the field equipment is monitored by this application. The operational status of the field equipment is reported to operations personnel. | Traffic Management Center |
| TMC Safeguard System Management | 'TMC Safeguard System Management' remotely monitors and controls safeguard systems for transportation facilities and infrastructure. Safeguard systems include blast shielding, exhaust systems and other automatic or remotely controlled systems intended to mitigate the impact of an incident. When access to a transportation facility is impacted by the activation of a safeguard system, impacted systems and travelers are notified. | Traffic Management Center |
| TMC Traffic Information Dissemination | 'TMC Traffic Information Dissemination' disseminates traffic and road conditions, closure and detour information, incident information, driver advisories, and other traffic-related data to other centers, the media, and driver information systems. It monitors and controls driver information system field equipment including dynamic message signs and highway advisory radio, managing dissemination of driver information through these systems. | Traffic Management Center |
| TMC Traffic Metering | 'TMC Traffic Metering' provides center monitoring and control of traffic metering systems including on ramps, through interchanges, and on the mainline roadway. All types of metering are covered including pre-timed/fixed time, time-based, dynamic and adaptive metering strategies and special bypasses. Metering rates can be calculated based upon historical data or current conditions including traffic, air quality, etc. | Traffic Management Center |
| Vehicle Basic Safety Communication | 'Vehicle Basic Safety Communication' exchanges current vehicle characteristics, location, and motion (including past and intended maneuver) information with other vehicles in the vicinity, uses that information to calculate vehicle paths, and warns the driver when the potential for an impending collision is detected. If available, map data is used to filter and interpret the relative location and motion of vehicles in the vicinity. Information from on-board sensors (e.g., radars and image processing) are also used, if available, in combination with the V2V communications to detect non-equipped vehicles and corroborate connected vehicle data. This object represents a broad range of implementations ranging from basic Vehicle Awareness Devices that only broadcast vehicle location and motion and provide no driver warnings to advanced integrated safety systems that coordinate maneuvers and may, in addition to warning the driver, provide collision warning information to support automated control functions that can support control intervention. | Vehicle |
| Vehicle Restricted Lanes Application | The 'Vehicle Restricted Lanes Application' monitors and reports its own operating parameters and communicates with roadside equipment to safely enter, operate within, and exit restricted lanes that are relevant to all types of vehicles. | Vehicle |
| Vehicle Traveler Information Reception | 'Vehicle Traveler Information Reception' receives advisories, vehicle signage data, and other driver information of use to all types of vehicles and drivers and presents this information to the driver using in-vehicle equipment. Information presented may include fixed sign information, traffic control device status (e.g., signal phase and timing data), advisory and detour information, warnings of adverse road and weather conditions, travel times, and other driver information. | Vehicle |
Includes Information Flows:
| Information Flow | Description |
|---|---|
| barrier system control | Information used to configure and control barrier systems that are represented by gates, barriers and other automated or remotely controlled systems used to manage entry to roadways. |
| barrier system coordination | The direct flow of information between field equipment. This includes information used to configure and control barrier systems that are represented by gates, barriers and other automated or remotely controlled systems used to manage entry to roadways. Current operating status of barrier systems is also shared including operating condition and current operational state. |
| barrier system status | Current operating status of barrier systems. Barrier systems represent gates, barriers and other automated or remotely controlled systems used to manage entry to roadways. Status of the systems includes operating condition and current operational state. |
| driver information | Regulatory, warning, guidance, and other information provided to the driver to support safe and efficient vehicle operation. |
| driver input | Driver input to the vehicle on-board equipment including configuration data, settings and preferences, interactive requests, and control commands. |
| driver updates | Information provided to the driver including visual displays, audible information and warnings, and haptic feedback. The updates inform the driver about current conditions, potential hazards, and the current status of vehicle on-board equipment. |
| dynamic sign coordination | The direct flow of information between field equipment. This includes information used to initialize, configure, and control dynamic message signs. This flow can provide message content and delivery attributes, local message store maintenance requests, control mode commands, status queries, and all other commands and associated parameters that support local management of these devices. Current operating status of dynamic message signs is returned. |
| equipment maintenance request | Identification of field equipment requiring repair and known information about the associated faults. |
| equipment maintenance status | Current status of field equipment maintenance actions. |
| infrastructure monitoring sensor control | Data used to configure and control infrastructure monitoring sensors. |
| infrastructure monitoring sensor data | Data read from infrastructure-based sensors that monitor the condition or integrity of transportation infrastructure including bridges, tunnels, interchanges, pavement, culverts, signs, transit rail or guideway, and other roadway infrastructure. Includes sensor data and the operational status of the sensors. |
| road network conditions | Current and forecasted traffic information, road and weather conditions, and other road network status. Either raw data, processed data, or some combination of both may be provided by this flow. Information on diversions and alternate routes, closures, and special traffic restrictions (lane/shoulder use, weight restrictions, width restrictions, HOV requirements) in effect is included. |
| roadway dynamic signage data | Information used to initialize, configure, and control dynamic message signs. This flow can provide message content and delivery attributes, local message store maintenance requests, control mode commands, status queries, and all other commands and associated parameters that support remote management of these devices. |
| roadway dynamic signage status | Current operating status of dynamic message signs. |
| safeguard system control | Data that controls safeguard systems (remotely controlled equipment used to mitigate the impact of incidents on transportation infrastructure, such as blast shields, exhaust systems, etc.). |
| safeguard system status | Current operating status of safeguard systems (remotely controlled equipment used to mitigate the impact of incidents on transportation infrastructure, such as blast shields, exhaust systems, etc.). Status of the systems includes operating condition and current operational state. |
| traffic detector control | Information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors. |
| traffic detector coordination | The direct flow of information between field equipment. This includes information used to configure and control traffic detector systems such as inductive loop detectors and machine vision sensors Raw and/or processed traffic detector data is returned that allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors |
| traffic detector data | Raw and/or processed traffic detector data which allows derivation of traffic flow variables (e.g., speed, volume, and density measures) and associated information (e.g., congestion, potential incidents). This flow includes the traffic data and the operational status of the traffic detectors |
| traffic image meta data | Meta data that describes traffic images. Traffic images (video) are in another flow. |
| traffic images | High fidelity, real-time traffic images suitable for surveillance monitoring by the operator or for use in machine vision applications. This flow includes the images. Meta data that describes the images is contained in another flow. |
| traffic metering control | Control commands and operating parameters for ramp meters, interchange meters, mainline meters, and other systems equipment associated with roadway metering operations. |
| traffic metering coordination | The direct flow of information between field equipment. This includes control commands and operating parameters for ramp meters, interchange meters, mainline meters, and other systems equipment associated with roadway metering operations. Current operational status of the traffic metering status is also provided. |
| traffic metering status | Current operational status and operating parameters for ramp meters, interchange meters, mainline meters and other control equipment associated with roadway metering operations. |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. |
| vehicle characteristics | The physical or visible characteristics of individual vehicles that can be used to detect, classify, and monitor vehicles and imaged to uniquely identify vehicles. |
| vehicle location and motion | Data describing the vehicle's location in three dimensions, heading, speed, acceleration, braking status, and size. |
| vehicle profile | Information about a vehicle such as vehicle make and model, fuel type, engine type, size and weight, vehicle performance and level of control automation, average emissions, average fuel consumption, passenger occupancy, or other data that can be used to classify vehicle eligibility for access to specific lanes, road segments, or regions or participation in cooperative vehicle control applications. |
| vehicle signage application info | In-vehicle signing application configuration data and messaging parameters. This flow provides a list of regulatory, warning, and information messages to be displayed and parameters that support scheduling and prioritizing messages to be issued to passing vehicles. This flow also supports remote control of the application so the application can be taken offline, reset, or restarted. |
| vehicle signage application status | In-vehicle signing application status reported by the RSE. This includes current operational state and status of the RSE and a log of messages sent to passing vehicles. |
| vehicle signage data | In-vehicle signing data that augments regulatory, warning, and informational road signs and signals. The information provided would include static sign information (e.g., stop, curve warning, guide signs, service signs, and directional signs) and dynamic information (e.g., local traffic and road conditions, restrictions, vehicle requirements, work zones, detours, closures, advisories, and warnings). |
| vehicle signage local data | Information provided by adjacent field equipment to support in-vehicle signing of dynamic information that is currently being displayed to passing drivers. This includes the dynamic information (e.g., local traffic and road conditions, work zone information, lane restrictions, detours, closures, advisories, parking availability, etc.) and control parameters that identify the desired timing, duration, and priority of the signage data. |
| video surveillance control | Information used to configure and control video surveillance systems. |
| video surveillance coordination | The direct flow of information between field equipment. This includes information used to configure and control video surveillance systems and the high fidelity, real-time traffic images and associated meta data that are returned. |
Goals and Objectives
Associated Planning Factors and Goals
| Planning Factor | Goal |
|---|---|
| A. Support the economic vitality of the metropolitan area, especially by enabling global competitiveness, productivity, and efficiency; | Improve freight network |
| B. Increase the safety of the transportation system for motorized and nonmotorized users; | Reduce fatalities and injuries |
| C. Increase the security of the transportation system for motorized and nonmotorized users; | Improve security |
| D. Increase the accessibility and mobility of people and for freight; | Reduce congestion |
| G. Promote efficient system management and operation; | Improve efficiency |
| I. Improve the resiliency and reliability of the transportation system and reduce or mitigate stormwater impacts of surface transportation; | Improve resiliency and reliability |
Associated Objective Categories 
Associated Objectives and Performance Measures 

Needs and Requirements
| Need | Functional Object | Requirement | ||
|---|---|---|---|---|
| 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. | Center Field Equipment Management | 01 | The center shall collect the status and fault data from field equipment, such as traffic, infrastructure, and environmental sensors, highway advisory radio and dynamic message signs, automated roadway treatment systems, barrier and safeguard systems, cameras, traffic signals and override equipment, ramp meters, short range communications equipment, security sensors and surveillance equipment, etc.. |
| 03 | The center shall provide control commands, configuration updates, software installation, or software upgrades for field devices under management of the center. | |||
| Roadway Basic Surveillance | 01 | The field element shall collect, process, digitize, and send traffic sensor data (speed, volume, and occupancy) to the center for further analysis and storage, under center control. | ||
| 02 | The field element shall collect, process, and send traffic images to the center for further analysis and distribution. | |||
| 04 | The field element shall return sensor and CCTV system operational status to the controlling center. | |||
| Roadway Infrastructure Monitoring | 02 | The field element shall include infrastructure condition monitoring sensors that monitor the condition of pavement, bridges, tunnels, associated hardware, and other transportation-related infrastructure (e.g., culverts), under maintenance vehicle control. | ||
| Roadway Traffic Metering | 01 | The field element shall regulate the flow of traffic on ramps, interchanges, and the mainline, under center control. | ||
| 03 | The field element shall return ramp, interchange, and mainline meter operational status to the controlling center. | |||
| 04 | The field element shall provide indications to the driver that the metering system is active and provide safe transitions between active and inactive status. | |||
| 05 | The field element shall return ramp, interchange, and mainline meter fault data to the maintenance center for repair. | |||
| TMC Basic Surveillance | 01 | The center shall monitor, analyze, and store traffic sensor data (speed, volume, occupancy) collected from field elements under remote control of the center. | ||
| TMC Traffic Information Dissemination | 01 | The center shall remotely control dynamic messages signs for dissemination of traffic and other information to drivers. | ||
| 02 | The center shall remotely control driver information systems that communicate directly from a center to the vehicle radio (such as Highway Advisory Radios) for dissemination of traffic and other information to drivers. | |||
| TMC Traffic Metering | 06 | The center shall monitor and control field equipment that supports traffic management in tunnels. | ||
| 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. | Center Field Equipment Management | 01 | The center shall collect the status and fault data from field equipment, such as traffic, infrastructure, and environmental sensors, highway advisory radio and dynamic message signs, automated roadway treatment systems, barrier and safeguard systems, cameras, traffic signals and override equipment, ramp meters, short range communications equipment, security sensors and surveillance equipment, etc.. |
| 03 | The center shall provide control commands, configuration updates, software installation, or software upgrades for field devices under management of the center. | |||
| Roadway Barrier System Control | 01 | The field element shall activate barrier systems for transportation facilities and infrastructure under center control. Barrier systems include automated or remotely controlled gates, barriers and other systems that manage entry to roadways. | ||
| 02 | The field element shall return barrier system operational status to the controlling center. | |||
| Roadway Safeguard System Control | 01 | The field element shall activate safeguard systems, equipment used to mitigate the impact of incidents on transportation infrastructure (e.g., blast shields, tunnel exhaust systems, etc.) under center control. | ||
| 02 | The field element shall return safeguard system operational status to the controlling center. | |||
| RSE Restricted Lanes Application | 01 | The field device shall collect vehicle profile information from vehicles entering the lanes and monitors vehicles within the lanes. | ||
| TMC Barrier System Management | 01 | The center shall remotely control barrier systems for transportation facilities and infrastructure. Barrier systems include automated or remotely controlled gates, barriers and other systems that manage entry to roadways. | ||
| 03 | The center shall collect barrier system operational status. | |||
| 04 | The center shall collect barrier system fault data and send to the maintenance center for repair. | |||
| TMC Safeguard System Management | 01 | The center shall remotely control safeguard systems, equipment used to mitigate the impact of incidents on transportation infrastructure (e.g., blast shields, tunnel exhaust systems, etc.) | ||
| 03 | The center shall collect safeguard system operational status. | |||
| 04 | The center shall collect safeguard system fault data and send to the maintenance center for repair. | |||
| TMC Traffic Metering | 02 | The center shall collect operational status from ramp meters, interchange meters, and mainline meters and compare against the control information sent by the center. | ||
| 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. | Roadway Traffic Information Dissemination | 02 | The field element shall include driver information systems that communicate directly from a center to the vehicle radio (such as Highway Advisory Radios) for dissemination of traffic and other information to drivers, under center control. |
| 05 | The field element shall provide dynamic message sign information to roadside equipment for transmission to connected vehicles to support in-vehicle signing. | |||
| RSE Restricted Lanes Application | 02 | The field device shall provide lane restriction information and signage data to vehicles. | ||
| RSE Traveler Information Communications | 01 | The field element shall distribute traveler information including traffic and road conditions or upcoming work zones to passing vehicles using short range communications, under center control. | ||
| 02 | The field element shall distribute advisory information, such as evacuation information, wide-area alerts, incident information, work zone intrusion information, recommended speed limit and other special information to passing vehicles using short range communications, under center control. | |||
| 15 | The field element shall provide real-time driving advice to connected vehicles to indicate whether they are allowed to enter the tunnel. | |||
| TMC In-Vehicle Signing Management | 01 | The center shall format and output sign information such as traffic and road conditions to field equipment that supports in-vehicle signage communications. | ||
| 02 | The center shall format and output advisory information, such as detour information, wide-area alerts, work zone intrusion information, and other special information to field equipment that supports in-vehicle signage communications. | |||
| Vehicle Basic Safety Communication | 06 | The vehicle shall exchange location and motion information with roadside equipment and nearby vehicles. | ||
| 07 | The vehicle shall receive warnings, informational road signs, traffic meters, and signals provided by infrastructure devices. | |||
| Vehicle Restricted Lanes Application | 01 | The vehicle shall provide operating parameters to the roadside in order to identify that it qualifies for use of a restricted lane. | ||
| 02 | The vehicle shall provide warnings and lane restrictions information to the driver. | |||
| Vehicle Traveler Information Reception | 02 | The vehicle shall receive advisory information, such as evacuation information, proximity to a maintenance and construction vehicle, wide-area alerts, work zone intrusion information, variable speed limits, tunnel entrance restrictions, border crossing advisories, and other special information. | ||
Security
In order to participate in this service package, each physical object should meet or exceed the following security levels.
| Physical Object Security | ||||
|---|---|---|---|---|
| Physical Object | Confidentiality | Integrity | Availability | Security Class |
| Connected Vehicle Roadside Equipment | Moderate | Moderate | Moderate | Class 2 |
| ITS Roadway Equipment | High | High | High | Class 5 |
| Maint and Constr Management Center | ||||
| Other ITS Roadway Equipment | High | High | Moderate | Class 4 |
| Other Traffic Management Centers | Low | Moderate | Moderate | Class 1 |
| Traffic Management Center | High | High | High | Class 5 |
| Vehicle | Low | High | Moderate | Class 3 |
| Vehicle Characteristics | ||||
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Source | Destination | Information Flow | Confidentiality | Integrity | Availability |
| Basis | Basis | Basis | |||
| Connected Vehicle Roadside Equipment | ITS Roadway Equipment | roadway dynamic signage data | Moderate | Moderate | Moderate |
| Device control information should not be available, as those with criminal intent may use this information toward their own ends. | Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. | Occasional outages of this flow will delay dissemination of the data to travelers (the eventual end user) which could have significant impacts on travel, both safety and mobility impacts. | |||
| Connected Vehicle Roadside Equipment | Traffic Management Center | vehicle signage application status | Moderate | Moderate | Low |
| This information could be of interest to a malicious individual who is attempting to determine the best way to accomplish a crime. As such it would be best to not make it easily accessible. DISC: WYO believes this to be LOW | If this is compromised, it could send unnecessary maintenance workers, or cause the appearance of excessive traffic violations, leading to further unnecessary investigation. | A delay in reporting this may cause a delay in necessary maintenance, but (a) this is not time-critical and (b) there are other channels for reporting malfunctioning. Additionally, there is a message received notification, which means that RSE can ensure that all intersection safety issues are delivered. | |||
| Connected Vehicle Roadside Equipment | Vehicle | vehicle signage data | Low | Moderate | Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It is meant to augment other signage data, and by definition is meant to be shared with everyone. | These signs are meant to augment other visual cues to the driver. They should be accurate, but any inaccuracies should be corrected for by other means. | These notifications are helpful to a driver, but if the driver does not receive this notification immediately, there should still be other visual cues. | |||
| Driver | Vehicle | driver input | Moderate | High | High |
| Data included in this flow may include origin and destination information, which should be protected from other's viewing as it may compromise the driver's privacy. | Commands from from the driver to the vehicle must be correct or the vehicle may behave in an unpredictable and possibly unsafe manner | Commands must always be able to be given or the driver has no control. | |||
| ITS Roadway Equipment | Connected Vehicle Roadside Equipment | roadway dynamic signage status | Moderate | Moderate | Moderate |
| Device status information should not be available, as those with criminal intent may use this information toward their own ends. | Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. | Failure of this flow affects traveler information dissemination, the importance of which varies with the data contained in the flow and the scenario. Could be LOW in many instances. | |||
| ITS Roadway Equipment | Connected Vehicle Roadside Equipment | vehicle signage local data | Low | Moderate | Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It is meant to augment other signage data, and by definition is meant to be shared with everyone. | This information impacts the vehicle signage data sent to neighboring ASDs and should be trusted to avoid sending wrong information. DISC: WYO believes this to be HIGH. | The system should know if these messages are not received. | |||
| ITS Roadway Equipment | Driver | driver information | Not Applicable | High | Moderate |
| This data is sent to all drivers and is also directly observable, by design. | This is the primary signal trusted by the driver to decide whether to go through the intersection and what speed to go through the intersection at; if it's wrong, accidents could happen. | If the lights are out you have to get a policeman to direct traffic – expensive and inefficient and may cause a cascading effect due to lack of coordination with other intersections. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | barrier system coordination | High | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | dynamic sign coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | traffic detector coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | traffic metering coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Other ITS Roadway Equipment | video surveillance coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| ITS Roadway Equipment | Traffic Management Center | barrier system status | Moderate | High | Moderate |
| Related to the control flow, however the data is directly observable and generally widely known. Difficult to justify obfuscation. | Status of barrier systems has direct human-safety related impact, that if performed incorrectly could lead to catastrophic incidents. | These systems need to operated when demanded or mobility will be restricted. However, manual processes should always be in place to compensate for a loss in connectivity, and to provide a secondary check for safety purposes anyway. | |||
| ITS Roadway Equipment | Traffic Management Center | infrastructure monitoring sensor data | High | Moderate | Moderate |
| Includes asset status and security-related monitoring both of which if available to a hostile third party would be useful in developing targets and inflicting damage. May be MODERATE if little such data is available or assets and potential impact is limited. | Real-time monitoring of transportation asset data should be accurate and timely to protect the monitored assets. Given that the destintation of this flow cannot act directly, it is difficult to justify HIGH, unless 'infrastructure situation data' does not exist. | As this flow includes data that reflects the condition of transportation assets, and can be used to infer the safety of use of those assets, loss of this flow means loss of asset safety monitoring, which has a potentially significant impact. | |||
| ITS Roadway Equipment | Traffic Management Center | roadway dynamic signage status | Moderate | Moderate | Moderate |
| Device status information should not be available, as those with criminal intent may use this information toward their own ends. | Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. | Failure of this flow affects traveler information dissemination, the importance of which varies with the data contained in the flow and the scenario. Could be LOW in many instances. | |||
| ITS Roadway Equipment | Traffic Management Center | safeguard system status | Moderate | High | Moderate |
| Related to the control flow, however the data is directly observable and generally widely known. Difficult to justify obfuscation. | Status of barrier systems has direct human-safety related impact, that if performed incorrectly could lead to catastrophic incidents. | These systems need to operated when demanded or mobility will be restricted. However, manual processes should always be in place to compensate for a loss in connectivity, and to provide a secondary check for safety purposes anyway. If no manual system exists, then some instances will be HIGH (for example, exhaust systems in tunnels). | |||
| ITS Roadway Equipment | Traffic Management Center | traffic detector data | Low | Moderate | Moderate |
| No impact if someone sees the data | Some minimal guarantee of data integrity is necessary for all C-ITS flows. THEA believes this to be LOW.only limited adverse effect if raw/processed traffic detector data is bad/compromised; DISC: WYO believes this to be HIGH | Only limited adverse effect of info is not timely/readily available, however without this information it will be difficult to perform traffic management activities, thus MODERATE. If not used for management, may be LOW. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic image meta data | Low | Moderate | Moderate |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. | While accuracy of this data is important for decision making purposes, applications should be able to cfunction without it. Thus MODERATE generally. | While accuracy of this data is important for decision making purposes, applications should be able to function without it. Thus MODERATE generally. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic images | Low | Moderate | Low |
| Traffic image data is generally intended for public consumption, and in any event is already video captured in the public arena, so this must be LOW. | Generally transportation coordination information should be correct between source and destination, or inappropriate actions may be taken. | While useful, there is no signficant impact if this flow is not available. | |||
| ITS Roadway Equipment | Traffic Management Center | traffic metering status | Moderate | Moderate | Moderate |
| Device status information should be concealed, as an unauthorized observer could use this to reverse engineer device control systems. | Device status information needs to be available and correct, or the controlling system may take inappropriate maintenance action, costing time and money. | Device status information needs to be available and correct, or the controlling system may take inappropriate maintenance action, costing time and money. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | barrier system coordination | High | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | dynamic sign coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | traffic detector coordination | Moderate | Moderate | Low |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | traffic metering coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other ITS Roadway Equipment | ITS Roadway Equipment | video surveillance coordination | Moderate | Moderate | Moderate |
| Any control flow has some confidentiality requirement, as observation of the flow may enable an attacker to analyze and learn how to assume control. MODERATE for most flows as the potential damage is likely contained, though anything that could have a significant safety impact may be assigned HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Since this directly impacts device control, we consider it the same as a control flow. Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Other Traffic Management Centers | Traffic Management Center | road network conditions | Low | Moderate | Moderate |
| No harm should come from seeing this data, as it is eventually intended for public consumption. | While accuracy of this data is important for decision making purposes, applications should be able to corroborate the data in many instances. Thus MODERATE generally. | Depends on the application; if mobility decisions that affect large numbers of travelers are made based on this data, then it is MODERATE. In more modest circumstances, it may be LOW. | |||
| Traffic Management Center | Connected Vehicle Roadside Equipment | vehicle signage application info | Moderate | Moderate | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | If this is compromised, it could send unnecessary maintenance workers, or cause the appearance of excessive traffic violations, or not properly communicate areas where maintenance workers are operating for example. Not HIGH because regardless of the application, this flow alone does not directly drive injury or damage. DISC: WYO believes this to be HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. This data should be received in a timely manner after it is sent. This will determine which lanes are blocked off for emergency vehicle use in incident management applications. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | ITS Roadway Equipment | barrier system control | Moderate | High | Moderate |
| Control flows need to be obfuscated, lest a hostile individual learn how to control these systems. Barrier systems in particular present a safety risk if compromised, and could have a significant safety and mobility impact. | Control of barrier systems has direct human-safety related impact, that if performed incorrectly could lead to catastrophic incidents. | These systems need to operated when demanded or mobility will be restricted. However, manual processes should always be in place to compensate for a loss in connectivity, and to provide a secondary check for safety purposes anyway. | |||
| Traffic Management Center | ITS Roadway Equipment | infrastructure monitoring sensor control | Moderate | High | Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: NYC believes this to be low: "This information is directly observable." | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. From NYC: The information sent from TMC directly affect the ITS-RE speed "announcement". | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From NYC: The ITS-RE can work accordingly or in fail-safe if information is not available. | |||
| Traffic Management Center | ITS Roadway Equipment | roadway dynamic signage data | Moderate | Moderate | Moderate |
| Device control information should not be available, as those with criminal intent may use this information toward their own ends. | Data is intended to feed dissemination channels, either C-ITS messages or DMS or other channels, so it should generally be correct as it is distributed widely and any forgery or corrupted data will have widespread impact. | Occasional outages of this flow will delay dissemination of the data to travelers (the eventual end user) which could have significant impacts on travel, both safety and mobility impacts. | |||
| Traffic Management Center | ITS Roadway Equipment | safeguard system control | High | High | High |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | ITS Roadway Equipment | traffic detector control | Moderate | Moderate | Low |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: THEA, WYO believe this to be LOW: encrypted, authenticated, proprietary; but should not cause severe damage if seen | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH.. From THEA: should be accurate and not be tampered with; could enable outside control of traffic sensors but should not cause severe harm, but could cause issues with traffic sensor data received and be detrimental to operations | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From THEA: want updates but delayed information will not be severe; should be able to operate from a previous/default control/config. DISC: WYO believes this to be MODERATE | |||
| Traffic Management Center | ITS Roadway Equipment | traffic metering control | Moderate | High | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | ITS Roadway Equipment | video surveillance control | Moderate | Moderate | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH. | |||
| Traffic Management Center | Other Traffic Management Centers | road network conditions | Low | Moderate | Moderate |
| encrypted; but no harm should come from seeing this data | info needs to be accurate and should not be tampered but should be able to cope with some bad data; should be able to confirm conditions by other mechanisms | condition info should be timely and readily available so that TMCs are aware of current traffic info, conditions, restrictions, etc. but should not have severe/catastrophic consequences if not | |||
| Traffic Management Center | Traffic Operations Personnel | traffic operator data | Moderate | Moderate | Moderate |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. | The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. | |||
| Traffic Operations Personnel | Traffic Management Center | traffic operator input | Moderate | High | High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Vehicle | Connected Vehicle Roadside Equipment | vehicle location and motion | Not Applicable | High | Moderate |
| This data is intentionally transmitted to everyone via a broadcast. Much of its information content can also be determined via other visual indicators | Incorrect information could lead to the system not operating properly. If the system does not properly know where the vehicle is, it cannot make an accurate decision about whether there is going to be a pedestrian in the crosswalk that the vehicle is approaching. This can have a safety impact.; DISC: NYC believes this to be MODERATE | This data is required for the system to operate properly. If this data is not available, the system cannot give accurate warning information. | |||
| Vehicle | Connected Vehicle Roadside Equipment | vehicle profile | Low | Moderate | Moderate |
| Includes no PII and probably includes information that could be observed, so no need for obfuscation. | As this information will be used to determine the vehicle's ability to access services or be charged usage fees, it must be correct and not easily forgeable. | This flow enables various services; if the flow is not available the vehicle may not be able to use those services, and also may be charged incorrectly. | |||
| Vehicle | Driver | driver updates | Not Applicable | Moderate | Moderate |
| This data is informing the driver about the safety of a nearby area. It should not contain anything sensitive, and does not matter if another person can observe it. | This is the information that is presented to the driver. If they receive incorrect information, they may act in an unsafe manner. However, there are other indicators that would alert them to any hazards, such as an oncoming vehicle or crossing safety lights. | If this information is not made available to the driver, then the system has not operated correctly. | |||
Standards
The following table lists the standards associated with physical objects in this service package. For standards related to interfaces, see the specific information flow triple pages. These pages can be accessed directly from the SVG diagram(s) located on the Physical tab, by clicking on each information flow line on the diagram.
| Name | Title | Physical Object |
|---|---|---|
| CTI 4001 RSU | Roadside Unit (RSU) Standard | Connected Vehicle Roadside Equipment |
| ITE 5201 ATC | Advanced Transportation Controller | ITS Roadway Equipment |
| ITE 5202 ATC Model 2070 | Model 2070 Controller Standard | ITS Roadway Equipment |
| ITE 5301 ATC ITS Cabinet | Intelligent Transportation System Standard Specification for Roadside Cabinets | ITS Roadway Equipment |
| ITE 5401 ATC API | Application Programming Interface Standard for the Advanced Transportation Controller | ITS Roadway Equipment |
| NEMA TS 8 Cyber and Physical Security | Cyber and Physical Security for Intelligent Transportation Systems | ITS Roadway Equipment |
| Traffic Management Center | ||
| NEMA TS2 Traffic Controller Assemblies | Traffic Controller Assemblies with NTCIP Requirements | ITS Roadway Equipment |
| NEMA TS4 Hardware Standards for DMS | Hardware Standards for Dynamic Message Signs (DMS) With NTCIP Requirements | ITS Roadway Equipment |
System Requirements
| System Requirement | Need | ||
|---|---|---|---|
| 001 | The system shall remotely control barrier systems for transportation facilities and infrastructure. Barrier systems include automated or remotely controlled gates, barriers and other systems that manage entry to roadways. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 002 | The system shall collect the status and fault data from field equipment, such as traffic, infrastructure, and environmental sensors, highway advisory radio and dynamic message signs, automated roadway treatment systems, barrier and safeguard systems, cameras, traffic signals and override equipment, ramp meters, short range communications equipment, security sensors and surveillance equipment, etc.. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. | ||
| 003 | The system shall collect barrier system fault data and send to the maintenance center for repair. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 004 | The system shall provide control commands, configuration updates, software installation, or software upgrades for field devices under management of the center. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. | ||
| 005 | The system shall monitor, analyze, and store traffic sensor data (speed, volume, occupancy) collected from field elements under remote control of the center. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 006 | The system shall format and output sign information such as traffic and road conditions to field equipment that supports in-vehicle signage communications. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 007 | The system shall format and output advisory information, such as detour information, wide-area alerts, work zone intrusion information, and other special information to field equipment that supports in-vehicle signage communications. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 008 | The system shall collect environmental sensor operational status. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 009 | The system shall exchange data with maintenance centers concerning the reporting of faulty equipment and the schedule/status of their repair. Information exchanged includes details of new equipment faults, and clearances when the faults are cleared. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 010 | The system shall remotely control safeguard systems, equipment used to mitigate the impact of incidents on transportation infrastructure (e.g., blast shields, tunnel exhaust systems, etc.) | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 011 | The system shall collect safeguard system operational status. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 012 | The system shall collect safeguard system fault data and send to the maintenance center for repair. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 013 | The system shall remotely control dynamic messages signs for dissemination of traffic and other information to drivers. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 014 | The system shall remotely control driver information systems that communicate directly from a center to the vehicle radio (such as Highway Advisory Radios) for dissemination of traffic and other information to drivers. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 015 | The system shall collect operational status from ramp meters, interchange meters, and mainline meters and compare against the control information sent by the center. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 016 | The system shall monitor and control field equipment that supports traffic management in tunnels. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 017 | The system shall activate barrier systems for transportation facilities and infrastructure under center control. Barrier systems include automated or remotely controlled gates, barriers and other systems that manage entry to roadways. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 018 | The system shall collect, process, digitize, and send traffic sensor data (speed, volume, and occupancy) to the center for further analysis and storage, under center control. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 019 | The system shall collect, process, and send traffic images to the center for further analysis and distribution. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 020 | The system shall return barrier system operational status to the controlling center. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 021 | The system shall return sensor and CCTV system operational status to the controlling center. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 022 | The system shall collect, process, and send traffic images to the center for further analysis and distribution. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 023 | The system shall include infrastructure condition monitoring sensors that monitor the condition of pavement, bridges, tunnels, associated hardware, and other transportation-related infrastructure (e.g., culverts), under maintenance vehicle control. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 024 | The system shall activate safeguard systems, equipment used to mitigate the impact of incidents on transportation infrastructure (e.g., blast shields, tunnel exhaust systems, etc.) under center control. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 025 | The system shall return safeguard system operational status to the controlling center. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 026 | The system shall include driver information systems that communicate directly from a center to the vehicle radio (such as Highway Advisory Radios) for dissemination of traffic and other information to drivers, under center control. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 027 | The system shall provide dynamic message sign information to roadside equipment for transmission to connected vehicles to support in-vehicle signing. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 028 | The system shall regulate the flow of traffic on ramps, interchanges, and the mainline, under center control. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 029 | The system shall return ramp, interchange, and mainline meter operational status to the controlling center. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 030 | The system shall provide indications to the driver that the metering system is active and provide safe transitions between active and inactive status. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 031 | The system shall return ramp, interchange, and mainline meter fault data to the maintenance center for repair. | 01 | Traffic operations need to be able to monitor and control field equipment that supports traffic management in tunnels. |
| 032 | The system shall collect vehicle profile information from vehicles entering the lanes and monitors vehicles within the lanes. | 02 | Traffic operations need to be able to monitor and control tunnel safety equipment in order to provide safe tunnel traffic operations. |
| 033 | The system shall provide lane restriction information and signage data to vehicles. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 034 | The system shall distribute traveler information including traffic and road conditions or upcoming work zones to passing vehicles using short range communications, under center control. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 035 | The system shall distribute advisory information, such as evacuation information, wide-area alerts, incident information, work zone intrusion information, recommended speed limit and other special information to passing vehicles using short range communications, under center control. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 036 | The system shall provide real-time driving advice to connected vehicles to indicate whether they are allowed to enter the tunnel. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 037 | The system shall exchange location and motion information with roadside equipment and nearby vehicles. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 038 | The system shall receive warnings, informational road signs, traffic meters, and signals provided by infrastructure devices. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 039 | The system shall provide operating parameters to the roadside in order to identify that it qualifies for use of a restricted lane. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 040 | The system shall provide warnings and lane restrictions information to the driver. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |
| 041 | The system shall receive advisory information, such as evacuation information, proximity to a maintenance and construction vehicle, wide-area alerts, work zone intrusion information, variable speed limits, tunnel entrance restrictions, and other special information. | 03 | Traffic operations need to be able to inform drivers of any traffic or safety issues prior to entering the tunnel. |