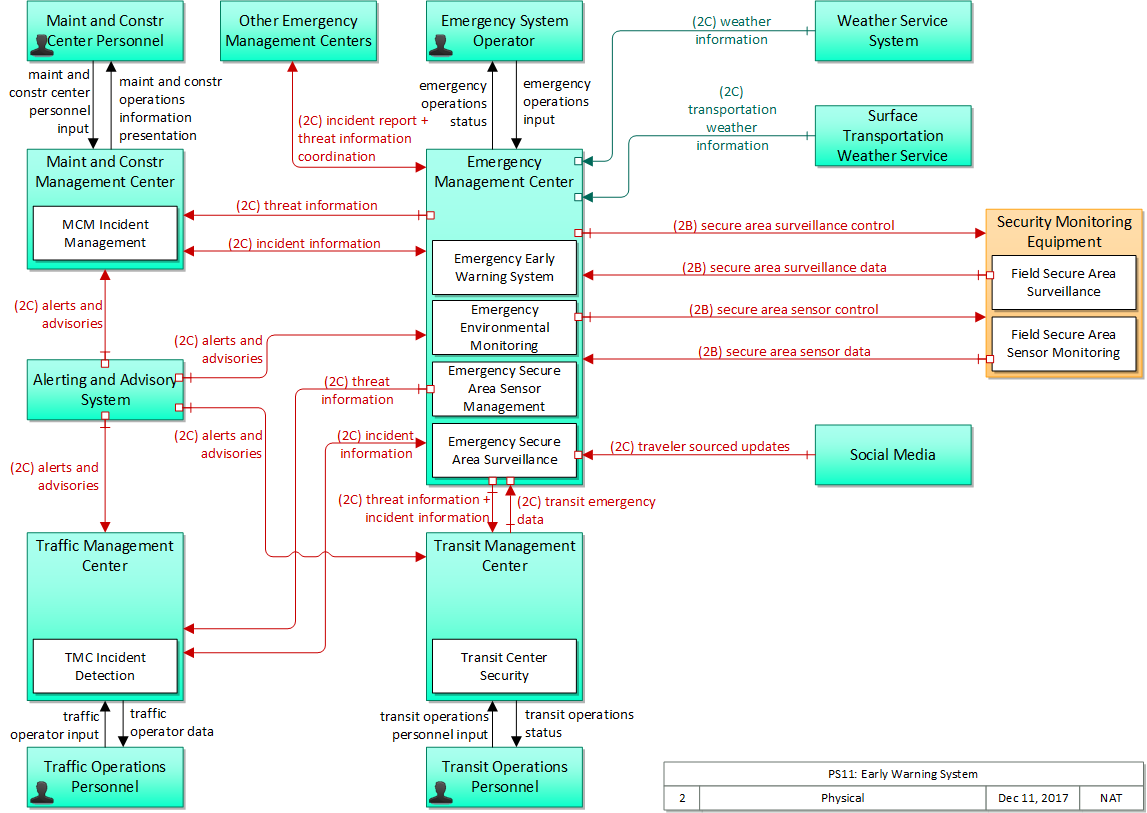
PS11: Early Warning System
This service package monitors and detects potential, looming, and actual disasters including natural disasters (hurricanes, earthquakes, floods, winter storms, tsunamis, etc.) and technological and man-made disasters (hazardous materials incidents, nuclear power plant accidents, and acts of terrorism including nuclear, chemical, biological, and radiological weapons attacks). The service package monitors alerting and advisory systems, ITS sensors and surveillance systems, field reports, and emergency call-taking systems to identify emergencies and notifies all responding agencies of detected emergencies.
Relevant Regions: Australia, Canada, European Union, and United States
- Enterprise
- Functional
- Physical
- Goals and Objectives
- Needs and Requirements
- Sources
- Security
- Standards
- System Requirements
Enterprise
Development Stage Roles and Relationships
Installation Stage Roles and Relationships
Operations and Maintenance Stage Roles and Relationships
(hide)
| Source | Destination | Role/Relationship |
|---|---|---|
| Alerting and Advisory System Maintainer | Alerting and Advisory System | Maintains |
| Alerting and Advisory System Manager | Alerting and Advisory System | Manages |
| Alerting and Advisory System Owner | Alerting and Advisory System Maintainer | System Maintenance Agreement |
| Alerting and Advisory System Owner | Alerting and Advisory System Manager | Operations Agreement |
| Alerting and Advisory System Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Alerting and Advisory System Owner | Emergency Management Center Owner | Information Provision Agreement |
| Alerting and Advisory System Owner | Emergency Management Center User | Service Usage Agreement |
| Alerting and Advisory System Owner | Emergency System Operator | Application Usage Agreement |
| Alerting and Advisory System Owner | Maint and Constr Center Personnel | Application Usage Agreement |
| Alerting and Advisory System Owner | Maint and Constr Management Center Maintainer | Maintenance Data Exchange Agreement |
| Alerting and Advisory System Owner | Maint and Constr Management Center Owner | Information Provision Agreement |
| Alerting and Advisory System Owner | Maint and Constr Management Center User | Service Usage Agreement |
| Alerting and Advisory System Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| Alerting and Advisory System Owner | Traffic Management Center Owner | Information Provision Agreement |
| Alerting and Advisory System Owner | Traffic Management Center User | Service Usage Agreement |
| Alerting and Advisory System Owner | Traffic Operations Personnel | Application Usage Agreement |
| Alerting and Advisory System Owner | Transit Management Center Maintainer | Maintenance Data Exchange Agreement |
| Alerting and Advisory System Owner | Transit Management Center Owner | Information Provision Agreement |
| Alerting and Advisory System Owner | Transit Management Center User | Service Usage Agreement |
| Alerting and Advisory System Owner | Transit Operations Personnel | Application Usage Agreement |
| Alerting and Advisory System Supplier | Alerting and Advisory System Owner | Warranty |
| Emergency Management Center Maintainer | Emergency Management Center | Maintains |
| Emergency Management Center Manager | Emergency Management Center | Manages |
| Emergency Management Center Manager | Emergency System Operator | System Usage Agreement |
| Emergency Management Center Owner | Emergency Management Center Maintainer | System Maintenance Agreement |
| Emergency Management Center Owner | Emergency Management Center Manager | Operations Agreement |
| Emergency Management Center Owner | Maint and Constr Center Personnel | Application Usage Agreement |
| Emergency Management Center Owner | Maint and Constr Management Center Maintainer | Maintenance Data Exchange Agreement |
| Emergency Management Center Owner | Maint and Constr Management Center Owner | Information Exchange Agreement |
| Emergency Management Center Owner | Maint and Constr Management Center User | Service Usage Agreement |
| Emergency Management Center Owner | Other Emergency Management Centers Maintainer | Maintenance Data Exchange Agreement |
| Emergency Management Center Owner | Other Emergency Management Centers Owner | Information Exchange Agreement |
| Emergency Management Center Owner | Other Emergency Management Centers User | Service Usage Agreement |
| Emergency Management Center Owner | Security Monitoring Equipment Maintainer | Maintenance Data Exchange Agreement |
| Emergency Management Center Owner | Security Monitoring Equipment Owner | Information Provision Agreement |
| Emergency Management Center Owner | Security Monitoring Equipment User | Service Usage Agreement |
| Emergency Management Center Owner | Traffic Management Center Maintainer | Maintenance Data Exchange Agreement |
| Emergency Management Center Owner | Traffic Management Center Owner | Information Exchange Agreement |
| Emergency Management Center Owner | Traffic Management Center User | Service Usage Agreement |
| Emergency Management Center Owner | Traffic Operations Personnel | Application Usage Agreement |
| Emergency Management Center Owner | Transit Management Center Maintainer | Maintenance Data Exchange Agreement |
| Emergency Management Center Owner | Transit Management Center Owner | Information Exchange Agreement |
| Emergency Management Center Owner | Transit Management Center User | Service Usage Agreement |
| Emergency Management Center Owner | Transit Operations Personnel | Application Usage Agreement |
| Emergency Management Center Supplier | Emergency Management Center Owner | Warranty |
| Emergency System Operator | Emergency Management Center | Operates |
| Maint and Constr Center Personnel | Maint and Constr Management Center | Operates |
| Maint and Constr Management Center Maintainer | Maint and Constr Management Center | Maintains |
| Maint and Constr Management Center Manager | Maint and Constr Center Personnel | System Usage Agreement |
| Maint and Constr Management Center Manager | Maint and Constr Management Center | Manages |
| Maint and Constr Management Center Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Maint and Constr Management Center Owner | Emergency Management Center Owner | Information Exchange Agreement |
| Maint and Constr Management Center Owner | Emergency Management Center User | Service Usage Agreement |
| Maint and Constr Management Center Owner | Emergency System Operator | Application Usage Agreement |
| Maint and Constr Management Center Owner | Maint and Constr Management Center Maintainer | System Maintenance Agreement |
| Maint and Constr Management Center Owner | Maint and Constr Management Center Manager | Operations Agreement |
| Maint and Constr Management Center Supplier | Maint and Constr Management Center Owner | Warranty |
| Other Emergency Management Centers Maintainer | Other Emergency Management Centers | Maintains |
| Other Emergency Management Centers Manager | Other Emergency Management Centers | Manages |
| Other Emergency Management Centers Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Other Emergency Management Centers Owner | Emergency Management Center Owner | Information Exchange Agreement |
| Other Emergency Management Centers Owner | Emergency Management Center User | Service Usage Agreement |
| Other Emergency Management Centers Owner | Emergency System Operator | Application Usage Agreement |
| Other Emergency Management Centers Owner | Other Emergency Management Centers Maintainer | System Maintenance Agreement |
| Other Emergency Management Centers Owner | Other Emergency Management Centers Manager | Operations Agreement |
| Other Emergency Management Centers Supplier | Other Emergency Management Centers Owner | Warranty |
| Security Monitoring Equipment Maintainer | Security Monitoring Equipment | Maintains |
| Security Monitoring Equipment Manager | Security Monitoring Equipment | Manages |
| Security Monitoring Equipment Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Security Monitoring Equipment Owner | Emergency Management Center Owner | Information Exchange and Action Agreement |
| Security Monitoring Equipment Owner | Emergency Management Center User | Service Usage Agreement |
| Security Monitoring Equipment Owner | Emergency System Operator | Application Usage Agreement |
| Security Monitoring Equipment Owner | Security Monitoring Equipment Maintainer | System Maintenance Agreement |
| Security Monitoring Equipment Owner | Security Monitoring Equipment Manager | Operations Agreement |
| Security Monitoring Equipment Supplier | Security Monitoring Equipment Owner | Warranty |
| Social Media Maintainer | Social Media | Maintains |
| Social Media Manager | Social Media | Manages |
| Social Media Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Social Media Owner | Emergency Management Center Owner | Information Provision Agreement |
| Social Media Owner | Emergency Management Center User | Service Usage Agreement |
| Social Media Owner | Emergency System Operator | Application Usage Agreement |
| Social Media Owner | Social Media Maintainer | System Maintenance Agreement |
| Social Media Owner | Social Media Manager | Operations Agreement |
| Social Media Supplier | Social Media Owner | Warranty |
| Surface Transportation Weather Service Maintainer | Surface Transportation Weather Service | Maintains |
| Surface Transportation Weather Service Manager | Surface Transportation Weather Service | Manages |
| Surface Transportation Weather Service Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Surface Transportation Weather Service Owner | Emergency Management Center Owner | Information Provision Agreement |
| Surface Transportation Weather Service Owner | Emergency Management Center User | Service Usage Agreement |
| Surface Transportation Weather Service Owner | Emergency System Operator | Application Usage Agreement |
| Surface Transportation Weather Service Owner | Surface Transportation Weather Service Maintainer | System Maintenance Agreement |
| Surface Transportation Weather Service Owner | Surface Transportation Weather Service Manager | Operations Agreement |
| Surface Transportation Weather Service Supplier | Surface Transportation Weather Service Owner | Warranty |
| Traffic Management Center Maintainer | Traffic Management Center | Maintains |
| Traffic Management Center Manager | Traffic Management Center | Manages |
| Traffic Management Center Manager | Traffic Operations Personnel | System Usage Agreement |
| Traffic Management Center Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Traffic Management Center Owner | Emergency Management Center Owner | Information Exchange Agreement |
| Traffic Management Center Owner | Emergency Management Center User | Service Usage Agreement |
| Traffic Management Center Owner | Emergency System Operator | Application Usage Agreement |
| Traffic Management Center Owner | Traffic Management Center Maintainer | System Maintenance Agreement |
| Traffic Management Center Owner | Traffic Management Center Manager | Operations Agreement |
| Traffic Management Center Supplier | Traffic Management Center Owner | Warranty |
| Traffic Operations Personnel | Traffic Management Center | Operates |
| Transit Management Center Maintainer | Transit Management Center | Maintains |
| Transit Management Center Manager | Transit Management Center | Manages |
| Transit Management Center Manager | Transit Operations Personnel | System Usage Agreement |
| Transit Management Center Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Transit Management Center Owner | Emergency Management Center Owner | Information Exchange Agreement |
| Transit Management Center Owner | Emergency Management Center User | Service Usage Agreement |
| Transit Management Center Owner | Emergency System Operator | Application Usage Agreement |
| Transit Management Center Owner | Transit Management Center Maintainer | System Maintenance Agreement |
| Transit Management Center Owner | Transit Management Center Manager | Operations Agreement |
| Transit Management Center Supplier | Transit Management Center Owner | Warranty |
| Transit Operations Personnel | Transit Management Center | Operates |
| Weather Service System Maintainer | Weather Service System | Maintains |
| Weather Service System Manager | Weather Service System | Manages |
| Weather Service System Owner | Emergency Management Center Maintainer | Maintenance Data Exchange Agreement |
| Weather Service System Owner | Emergency Management Center Owner | Information Provision Agreement |
| Weather Service System Owner | Emergency Management Center User | Service Usage Agreement |
| Weather Service System Owner | Emergency System Operator | Application Usage Agreement |
| Weather Service System Owner | Weather Service System Maintainer | System Maintenance Agreement |
| Weather Service System Owner | Weather Service System Manager | Operations Agreement |
| Weather Service System Supplier | Weather Service System Owner | Warranty |
Functional
This service package includes the following Functional View PSpecs:
Physical
The physical diagram can be viewed in SVG or PNG format and the current format is SVG.SVG Diagram
PNG Diagram
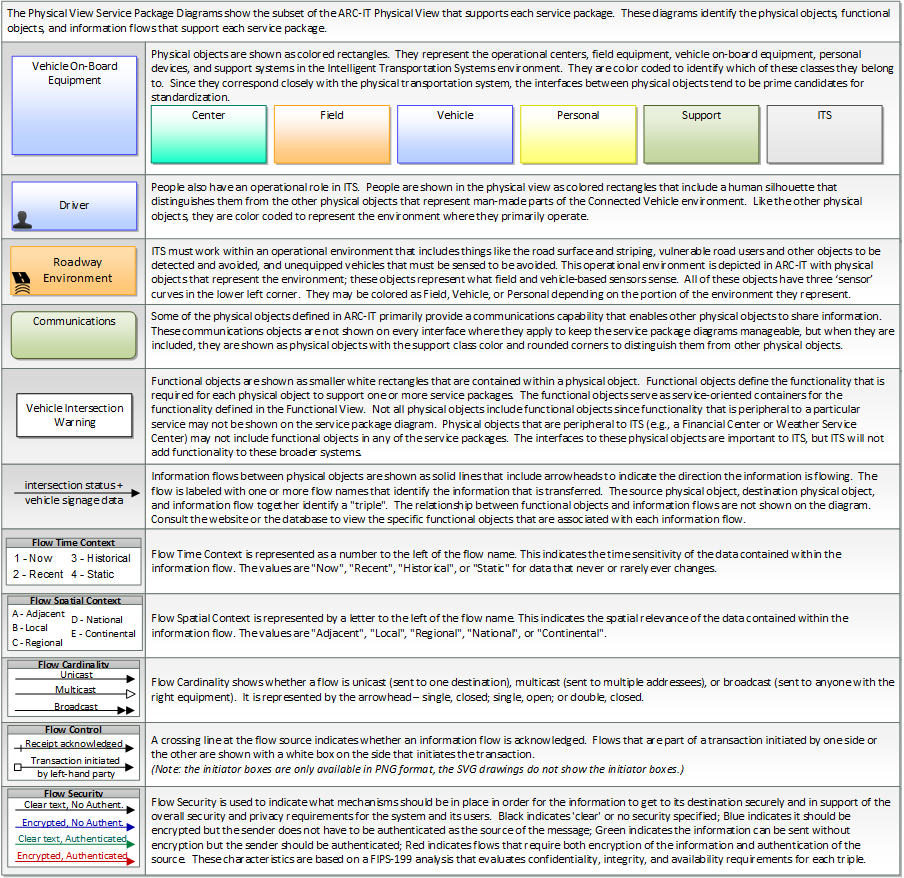
Includes Physical Objects:
| Physical Object | Class | Description |
|---|---|---|
| Alerting and Advisory System | Center | 'Alerting and Advisory System' represents the federal, state, and local alerting and advisory systems that provide alerts, advisories, and other potential threat information that is relevant to surface transportation systems. This includes systems such as the Information Sharing and Analysis Centers (ISACS), the National Infrastructure Protection Center (NIPC), the Homeland Security Advisory System (HSAS), and other systems that provide intelligence about potential, imminent, or actual attacks on the transportation infrastructure or its supporting information systems. This system also represents the early warning and emergency alert systems operated by federal, state, county, and local agencies that provide advisories and alerts regarding all types of emergencies including natural hazards (floods, hurricanes, tornados, earthquakes), accidents (chemical spills, nuclear power plant emergencies) and other civil emergencies such as child abduction alerts that impact transportation system operation and/or require immediate public notification. Note that weather related watches and warnings, such as those issued by the National Hurricane Center, are provided by both this terminator and the Weather Service terminator since many alerting and advisory systems and the National Weather Service both provide severe weather and related hazards information. The alerts and advisories that are provided by the systems represented by this terminator are based on analysis of potential threat information that is collected from a variety of sources, including information collected by ITS systems. The bidirectional interface with this terminator allows potential threat information that is collected by ITS systems to be provided to the alerting and advisory systems to improve their ability to identify threats and provide useful and timely information. The types of information provided by this terminator include general assessments and incident awareness information, advisories that identify potential threats or recommendations to increase preparedness levels, alerts regarding imminent or in-progress emergencies, and specific threat information such as visual imagery used for biometric image processing. |
| Emergency Management Center | Center | The 'Emergency Management Center' represents systems that support incident management, disaster response and evacuation, security monitoring, and other security and public safety-oriented ITS applications. It includes the functions associated with fixed and mobile public safety communications centers including public safety call taker and dispatch centers operated by police (including transit police), fire, and emergency medical services. It includes the functions associated with Emergency Operations Centers that are activated at local, regional, state, and federal levels for emergencies and the portable and transportable systems that support Incident Command System operations at an incident. This Center also represents systems associated with towing and recovery, freeway service patrols, HAZMAT response teams, and mayday service providers. It manages sensor and surveillance equipment used to enhance transportation security of the roadway infrastructure (including bridges, tunnels, interchanges, and other key roadway segments) and the public transportation system (including transit vehicles, public areas such as transit stops and stations, facilities such as transit yards, and transit infrastructure such as rail, bridges, tunnels, or bus guideways). It provides security/surveillance services to improve traveler security in public areas not a part of the public transportation system. It monitors alerts, advisories, and other threat information and prepares for and responds to identified emergencies. It coordinates emergency response involving multiple agencies with peer centers. It stores, coordinates, and utilizes emergency response and evacuation plans to facilitate this coordinated response. Emergency situation information including damage assessments, response status, evacuation information, and resource information are shared The Emergency Management Center also provides a focal point for coordination of the emergency and evacuation information that is provided to the traveling public, including wide-area alerts when immediate public notification is warranted. It tracks and manages emergency vehicle fleets using real-time road network status and routing information from the other centers to aid in selecting the emergency vehicle(s) and routes, and works with other relevant centers to tailor traffic control to support emergency vehicle ingress and egress, implementation of special traffic restrictions and closures, evacuation traffic control plans, and other special strategies that adapt the transportation system to better meet the unique demands of an emergency. |
| Emergency System Operator | Center | 'Emergency System Operator' represents the public safety personnel that monitor emergency requests, (including those from the E911 Operator) and set up pre-defined responses to be executed by an emergency management system. The operator may also override predefined responses where it is observed that they are not achieving the desired result. This also includes dispatchers who manage an emergency fleet (police, fire, ambulance, HAZMAT, etc.) or higher order emergency managers who provide response coordination during emergencies. |
| Maint and Constr Center Personnel | Center | The people that directly interface with a Maintenance and Construction Management Center. These personnel interact with fleet dispatch and management systems, road maintenance systems, incident management systems, work plan scheduling systems, and work zone management systems. They provide operator data and command inputs to direct system operations to varying degrees depending on the type of system and the deployment scenario. |
| Maint and Constr Management Center | Center | The 'Maint and Constr Management Center' monitors and manages roadway infrastructure construction and maintenance activities. Representing both public agencies and private contractors that provide these functions, this physical object manages fleets of maintenance, construction, or special service vehicles (e.g., snow and ice control equipment). The physical object receives a wide range of status information from these vehicles and performs vehicle dispatch, routing, and resource management for the vehicle fleets and associated equipment. The physical object participates in incident response by deploying maintenance and construction resources to an incident scene, in coordination with other center physical objects. The physical object manages equipment at the roadside, including environmental sensors and automated systems that monitor and mitigate adverse road and surface weather conditions. It manages the repair and maintenance of both non-ITS and ITS equipment including the traffic controllers, detectors, dynamic message signs, signals, and other equipment associated with the roadway infrastructure. Weather information is collected and fused with other data sources and used to support advanced decision support systems. The physical object remotely monitors and manages ITS capabilities in work zones, gathering, storing, and disseminating work zone information to other systems. It manages traffic in the vicinity of the work zone and advises drivers of work zone status (either directly at the roadside or through an interface with the Transportation Information Center or Traffic Management Center physical objects.) Construction and maintenance activities are tracked and coordinated with other systems, improving the quality and accuracy of information available regarding closures and other roadway construction and maintenance activities. |
| Other Emergency Management Centers | Center | 'Other Emergency Management Centers' provides a source and destination for information flows between various communications centers operated by public safety agencies, emergency management agencies, other allied agencies, and private companies that participate in coordinated management of transportation-related incidents, including disasters. The interface represented by this object enables emergency management activities to be coordinated across jurisdictional boundaries and between functional areas, supporting requirements for general networks connecting many allied agencies. It also supports interface to other allied agencies like utility companies that also participate in the coordinated response to selected highway-related incidents. |
| Security Monitoring Equipment | Field | 'Security Monitoring Equipment' includes surveillance and sensor equipment used to provide enhanced security and safety for transportation facilities or infrastructure. The equipment is located in non-public areas of transportation facilities (e.g. maintenance and transit yards), on or near non-roadway parts of the transportation infrastructure (e.g. transit railway and guideways), and in public areas (e.g., transit stops, transit stations, intermodal terminals). This equipment also includes surveillance and sensor equipment located on or near major roadway features such as bridges, tunnels, and interchanges, when the equipment's primary function is one of security and safety. If the primary function of the equipment is traffic surveillance or incident detection, then the surveillance or sensors would be covered as part of the 'ITS Roadway Equipment'. The surveillance equipment includes video (e.g. CCTV cameras) and/or audio systems. The sensor equipment includes threat sensors (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), object detection (e.g. metal detectors), intrusion or motion detection, and infrastructure integrity monitoring (e.g. rail track continuity checking or bridge structural integrity monitoring). Limited processing of collected sensor and surveillance data is also included in this subsystem to support threat detection and classification. |
| Social Media | Center | 'Social Media' provides forums for social interaction and opportunities for gathering and distributing traveler information. These sites provide crowd sourced information and the opportunity to provide traveler information to specific communities of interest. Examples include Facebook, Twitter, and LinkedIn. Each social media platform offers its own tools and API that allow integration of web content into a shared social media experience. |
| Surface Transportation Weather Service | Center | The 'Surface Transportation Weather Service' represents the providers of value-added sector-specific meteorological services. These providers utilize National Weather Service data and predictions, road condition information and local environmental data provided by traffic management or maintenance organizations, and their own models to provide surface transportation related weather observations and forecasts including pavement temperature and conditions. |
| Traffic Management Center | Center | The 'Traffic Management Center' monitors and controls traffic and the road network. It represents centers that manage a broad range of transportation facilities including freeway systems, rural and suburban highway systems, and urban and suburban traffic control systems. It communicates with ITS Roadway Equipment and Connected Vehicle Roadside Equipment (RSE) to monitor and manage traffic flow and monitor the condition of the roadway, surrounding environmental conditions, and field equipment status. It manages traffic and transportation resources to support allied agencies in responding to, and recovering from, incidents ranging from minor traffic incidents through major disasters. |
| Traffic Operations Personnel | Center | 'Traffic Operations Personnel' represents the people that operate a traffic management center. These personnel interact with traffic control systems, traffic surveillance systems, incident management systems, work zone management systems, and travel demand management systems. They provide operator data and command inputs to direct system operations to varying degrees depending on the type of system and the deployment scenario. |
| Transit Management Center | Center | The 'Transit Management Center' manages transit vehicle fleets and coordinates with other modes and transportation services. It provides operations, maintenance, customer information, planning and management functions for the transit property. It spans distinct central dispatch and garage management systems and supports the spectrum of fixed route, flexible route, paratransit services, transit rail, and bus rapid transit (BRT) service. The physical object's interfaces support communication between transit departments and with other operating entities such as emergency response services and traffic management systems. |
| Transit Operations Personnel | Center | 'Transit Operations Personnel' represents the people that are responsible for fleet management, maintenance operations, and scheduling activities of the transit system. These different roles represent a variety of individuals in the transit industry. Within the transit industry the person responsible for fleet management is known by many names: Street Supervisor, Starter, Dispatcher, Supervisor, Traffic Controller, Transportation Coordinator. This person actively monitors, controls, and modifies the transit fleet routes and schedules on a day to day basis (dynamic scheduling). The modifications will take account of abnormal situations such as vehicle breakdown, vehicle delay, detours around work zones or incidents (detour management, connection protection, and service restoration), and other causes of route or schedule deviations. Transit operations personnel are also responsible for demand responsive transit operation and for managing emergency situations within the transit network such as silent alarms on board transit vehicles, or the remote disabling of the vehicle. In addition the Transit Operations Personnel may be responsible for assigning vehicle operators to routes, checking vehicle operators in and out, and managing transit stop issues. This object also represents the personnel in the transit garage that are responsible for maintenance of the transit fleets, including monitoring vehicle status, matching vehicles with operators, and maintenance checking of transit vehicles. Finally, it represents the people responsible for planning, development, and management of transit routes and schedules. |
| Weather Service System | Center | The 'Weather Service System' provides weather, hydrologic, and climate information and warnings of hazardous weather including thunderstorms, flooding, hurricanes, tornadoes, winter weather, tsunamis, and climate events. It provides atmospheric weather observations and forecasts that are collected and derived by the National Weather Service, private sector providers, and various research organizations. The interface provides formatted weather data products suitable for on-line processing and integration with other ITS data products as well as Doppler radar images, satellite images, severe storm warnings, and other products that are formatted for presentation to various ITS users. |
Includes Functional Objects:
| Functional Object | Description | Physical Object |
|---|---|---|
| Emergency Early Warning System | 'Emergency Early Warning System' monitors alerting and advisory systems, information collected by ITS surveillance and sensors, and reports from other agencies and uses this information to identify potential, imminent, or in-progress major incidents or disasters. Notification is provided to initiate the emergency response, including public notification using ITS traveler information systems, where appropriate. | Emergency Management Center |
| Emergency Environmental Monitoring | 'Emergency Environmental Monitoring' collects current and forecast road conditions and surface weather information from a variety of sources. The collected environmental information is monitored and presented to the operator and used to more effectively manage incidents. | Emergency Management Center |
| Emergency Secure Area Sensor Management | 'Emergency Secure Area Sensor Management' manages sensors that monitor secure areas in the transportation system, processes the collected data, performs threat analysis in which data is correlated with other sensor, surveillance, and advisory inputs, and then disseminates resultant threat information to emergency personnel and other agencies. In response to identified threats, the operator may request activation of barrier and safeguard systems to preclude an incident, control access during and after an incident or mitigate impact of an incident. The sensors may be in secure areas frequented by travelers (i.e., transit stops, transit stations, rest areas, park and ride lots, modal interchange facilities, on-board a transit vehicle, etc.) or around transportation infrastructure such as bridges, tunnels and transit railways or guideways. The types of sensors include acoustic, threat (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), infrastructure condition and integrity, motion and object sensors. | Emergency Management Center |
| Emergency Secure Area Surveillance | 'Emergency Secure Area Surveillance' monitors surveillance inputs from secure areas in the transportation system. The surveillance may be of secure areas frequented by travelers (i.e., transit stops, transit stations, rest areas, park and ride lots, modal interchange facilities, on-board a transit vehicle, etc.) or around transportation infrastructure such as bridges, tunnels and transit railways or guideways. It provides both video and audio surveillance information to emergency personnel and automatically alerts emergency personnel of potential incidents. | Emergency Management Center |
| Field Secure Area Sensor Monitoring | 'Field Secure Area Sensor Monitoring' includes sensors that monitor conditions of secure areas including facilities (e.g. transit yards), transportation infrastructure (e.g. Bridges, tunnels, interchanges, and transit railways or guideways), and public areas (e.g., transit stops, transit stations, rest areas, park and ride lots, modal interchange facilities). A range of acoustic, environmental threat (e.g. Chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), infrastructure condition and integrity and motion and object sensors are included. | Security Monitoring Equipment |
| Field Secure Area Surveillance | 'Field Secure Area Surveillance' includes video and audio surveillance equipment that monitors conditions of secure areas including facilities (e.g. transit yards), transportation infrastructure (e.g. as bridges, tunnels, interchanges, and transit railways or guideways), and public areas (e.g., transit stops, transit stations, rest areas, park and ride lots, modal interchange facilities). It provides the surveillance information to the Emergency Management Center for possible threat detection. It also provides local processing of the video or audio information, providing processed or analyzed results to the Emergency Management Center. | Security Monitoring Equipment |
| MCM Incident Management | 'MCM Incident Management' supports maintenance and construction participation in coordinated incident response. Incident notifications are shared, incident response resources are managed, and the overall incident situation and incident response status is coordinated among allied response organizations. | Maint and Constr Management Center |
| TMC Incident Detection | 'TMC Incident Detection' identifies and reports incidents to Traffic Operations Personnel. It remotely monitors and controls traffic sensor and surveillance systems that support incident detection and verification. It analyzes and reduces the collected sensor and surveillance data, external alerting and advisory and incident reporting systems, anticipated demand information from intermodal freight depots, border crossings, special event information, and identifies and reports incidents and hazardous conditions | Traffic Management Center |
| Transit Center Security | 'Transit Center Security' monitors transit vehicle operator or traveler activated alarms received from on-board a transit vehicle. It supports transit vehicle operator authentication and provides the capability to remotely disable a transit vehicle. It also includes the capability to alert operators and police to potential incidents identified by these security features. | Transit Management Center |
Includes Information Flows:
| Information Flow | Description |
|---|---|
| alerts and advisories | Assessments (general incident and vulnerability awareness information), advisories (identification of threats or recommendations to increase preparedness levels), and alerts (information on imminent or in-progress emergencies). This flow also provides supporting descriptive detail on incidents, threats, and vulnerabilities to increase preparedness and support effective response to threats against the surface transportation system. |
| emergency operations input | Emergency operator input supporting call taking, dispatch, emergency operations, security monitoring, and other operations and communications center operator functions. |
| emergency operations status | Presentation of information to the operator including emergency operations data, supporting a range of emergency operating positions including call taker, dispatch, emergency operations, security monitoring, and various other operations and communications center operator positions. |
| incident information | Notification of existence of incident and expected severity, location, time and nature of incident. As additional information is gathered and the incident evolves, updated incident information is provided. Incidents include any event that impacts transportation system operation ranging from routine incidents (e.g., disabled vehicle at the side of the road) through large-scale natural or human-caused disasters that involve loss of life, injuries, extensive property damage, and multi-jurisdictional response. This also includes special events, closures, and other planned events that may impact the transportation system. |
| incident report | Report of an identified incident including incident location, type, severity and other information necessary to initiate an appropriate incident response. |
| maint and constr center personnel input | User input from maintenance and construction center personnel including routing information, scheduling data, dispatch instructions, device configuration and control, resource allocations, alerts, incident and emergency response plan coordination. |
| maint and constr operations information presentation | Presentation of maintenance and construction operations information to center personnel. This information includes maintenance resource status (vehicles, equipment, and personnel), work schedule information, work status, road and weather conditions, traffic information, incident information and associated resource requests, security alerts, emergency response plans and a range of other information that supports efficient maintenance and construction operations and planning. |
| secure area sensor control | Information used to configure and control threat sensors (e.g., thermal, acoustic, radiological, chemical), object, motion and intrusion detection sensors. The provided information controls sensor data collection, aggregation, filtering, and other local processing. |
| secure area sensor data | Data provided by threat sensors (e.g., thermal, acoustic, radiological, chemical), and intrusion, motion, and object detection sensors in secure areas indicating the sensor's operational status, raw and processed sensor data, and alarm indicators when a threat has been detected. |
| secure area surveillance control | Information used to configure and control audio and video surveillance systems used for transportation infrastructure security in secure areas. The provided information controls surveillance data collection, aggregation, filtering, and other local processing. |
| secure area surveillance data | Data collected from surveillance systems used to monitor secure areas. Includes video, audio, processed surveillance data, equipment operational status, and alarm indicators when a threat has been detected. |
| threat information | Threats regarding transportation infrastructure, facilities, or systems detected by a variety of methods (sensors, surveillance, threat analysis of advisories from outside agencies, etc. |
| threat information coordination | Sensor, surveillance, and threat data including raw and processed data that is collected by sensor and surveillance equipment located in secure areas. |
| traffic operator data | Presentation of traffic operations data to the operator including traffic conditions, current operating status of field equipment, maintenance activity status, incident status, video images, security alerts, emergency response plan updates and other information. This data keeps the operator appraised of current road network status, provides feedback to the operator as traffic control actions are implemented, provides transportation security inputs, and supports review of historical data and preparation for future traffic operations activities. |
| traffic operator input | User input from traffic operations personnel including requests for information, configuration changes, commands to adjust current traffic control strategies (e.g., adjust signal timing plans, change DMS messages), and other traffic operations data entry. |
| transit emergency data | Initial notification of transit emergency at a transit stop or on transit vehicles and further coordination as additional details become available and the response is coordinated. |
| transit operations personnel input | User input from transit operations personnel including instructions governing service availability, schedules, emergency response plans, transit personnel assignments, transit maintenance requirements, and other inputs that establish general system operating requirements and procedures. |
| transit operations status | Presentation of information to transit operations personnel including accumulated schedule and fare information, ridership and on-time performance information, emergency response plans, transit personnel information, maintenance records, and other information intended to support overall planning and management of a transit property. |
| transportation weather information | Current and forecast road conditions and weather information (e.g., surface condition, flooding, wind advisories, visibility, etc.) associated with the transportation network. This information is of a resolution, timeliness, and accuracy to be useful in transportation decision making. |
| traveler sourced updates | Traveler posts on traffic and road conditions, parking availability, transit services, traveler services, shelter information, hazards, debris, obstacles, and other real-time crowd-sourced data that may be shared with other travelers. |
| weather information | Accumulated forecasted and current weather data (e.g., temperature, pressure, wind speed, wind direction, humidity, precipitation, visibility, light conditions, etc.). |
Goals and Objectives
Associated Planning Factors and Goals
| Planning Factor | Goal |
|---|---|
| C. Increase the security of the transportation system for motorized and nonmotorized users; | Improve security |
Associated Objective Categories 
| Objective Category |
|---|
| Security: Crime |
| Security: Terrorism, Natural Disasters, and Hazardous Material Incidents |
Associated Objectives and Performance Measures 

Needs and Requirements
| Need | Functional Object | Requirement | ||
|---|---|---|---|---|
| 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. | Emergency Early Warning System | 01 | The center shall monitor information from Alerting and Advisory Systems such as the Information Sharing and Analysis Centers (ISACs), the National Infrastructure Protection Center (NIPC), the Homeland Security Advisory System (HSAS), etc. The information may include assessments (general incident and vulnerability awareness information), advisories (identification of threats or recommendations to increase preparedness levels), or alerts (information on imminent or in-progress emergencies). |
| 02 | The center shall receive incident information from other transportation management centers to support the early warning system. | |||
| 03 | The center shall support the entry of alert and advisory information directly from the emergency system operator. | |||
| 04 | The center shall receive potential incident information from social media sources to support the early warning system. | |||
| 05 | The center shall provide the capability to correlate alerts and advisories, incident information, and security sensor and surveillance data. | |||
| 13 | The center shall process status information from each of the centers that have been sent the wide-area alert. | |||
| 15 | The center shall present the alert and advisory information and the status of the actions taken in response to the alert by the other centers to the emergency system operator as received from other system inputs. | |||
| Emergency Environmental Monitoring | 01 | The center shall collect current and forecast road and weather information from weather service providers (such as the National Weather Service and value-added sector specific meteorological services). | ||
| Emergency Secure Area Sensor Management | 01 | The center shall remotely monitor and control security sensor data collected in secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). The types of security sensor data include environmental threat (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), infrastructure condition and integrity, intrusion and motion, and object detection sensors. The data may be raw or pre-processed in the field. | ||
| 02 | The center shall remotely monitor and control security sensor data collected in traveler secure areas, which include transit stations, transit stops, rest areas, park and ride lots, and other fixed sites along travel routes (e.g., emergency pull-off areas and travel information centers). The types of security sensor data include environmental threat (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), intrusion and motion, and object detection sensors. The data may be raw or pre-processed in the field. | |||
| 05 | The center shall identify potential security threats based on collected security sensor data. | |||
| 06 | The center shall verify potential security threats by correlating security sensor data from multiple sources. | |||
| 07 | The center shall perform threat analysis based on correlations of security sensor and surveillance data. | |||
| 08 | The center shall exchange threat analysis data with Alerting and Advisory Systems and use that data in local threat analysis processing. | |||
| Emergency Secure Area Surveillance | 05 | The center shall identify potential security threats based on collected security surveillance data. | ||
| 06 | The center shall verify potential security threats by correlating security surveillance data from multiple sources. | |||
| Field Secure Area Sensor Monitoring | 01 | The field element shall include security sensors that monitor conditions of secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). | ||
| 02 | The field element sensor monitoring shall be remotely controlled by a center. | |||
| 06 | The field element shall include motion and intrusion detection sensors. | |||
| 09 | The field element shall remotely process security sensor data and provide an indication of potential incidents or threats to a center. | |||
| Field Secure Area Surveillance | 01 | The field element shall include video and/or audio surveillance of secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). | ||
| 02 | The field element shall be remotely controlled by a center. | |||
| 04 | The field element shall provide raw video or audio data. | |||
| 05 | The field element shall remotely process video and audio data and provide an indication of potential incidents or threats to a center. | |||
| MCM Incident Management | 02 | The maintenance center shall exchange alert information and status with emergency management centers. The information includes notification of a major emergency such as a natural or man-made disaster, civil emergency, or child abduction. The information may include the alert originator, the nature of the emergency, the geographic area affected by the emergency, the effective time period, etc. | ||
| TMC Incident Detection | 04 | The center shall exchange incident and threat information with emergency management centers as well as maintenance and construction centers; including notification of existence of incident and expected severity, location, time and nature of incident. | ||
| Transit Center Security | 07 | The center shall coordinate the response to security incidents involving transit with other agencies including Emergency Management, other transit agencies, media, traffic management, and traveler information service providers. | ||
| 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. | Emergency Early Warning System | 06 | The center shall broadcast wide-area alerts and advisories to traffic management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. |
| 07 | The center shall broadcast wide-area alerts and advisories to transit management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | |||
| 10 | The center shall broadcast wide-area alerts and advisories to maintenance centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | |||
| 11 | The center shall broadcast wide-area alerts and advisories to other emergency management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | |||
| 14 | The center shall coordinate the broadcast of wide-area alerts and advisories with other emergency management centers. | |||
| Emergency Environmental Monitoring | 04 | The center shall assimilate current and forecast road conditions and surface weather information to support incident management. | ||
| 05 | The center shall provide the road and weather warning and advisories to the emergency responders. | |||
| Emergency Secure Area Sensor Management | 09 | The center shall disseminate threat information to other agencies, including traffic, transit, maintenance, rail operations, and other emergency management centers. | ||
| MCM Incident Management | 01 | The maintenance center shall receive inputs from the Alerting and Advisory System concerning the possibility or occurrence of severe weather, terrorist activity, or other major emergency, including information provided by the Emergency Alert System. | ||
| TMC Incident Detection | 01 | The center shall receive inputs from the Alerting and Advisory System concerning the possibility or occurrence of severe weather, terrorist activity, or other major emergency, including information provided by the Emergency Alert System. | ||
| Transit Center Security | 05 | The center shall receive information pertaining to a wide-area alert such as weather alerts, disaster situations, or child abductions. This information may come from Emergency Management or from other Alerting and Advisory Systems. | ||
Related Sources
| Document Name | Version | Publication Date |
|---|---|---|
| ITS User Services Document | 1/1/2005 | |
| R.E.S.C.U.M.E. (Response, Emergency Staging and Communications, Uniform Management, and Evacuation) ConOps | Final | 11/19/2012 |
| R.E.S.C.U.M.E. Report on Functional and Performance Requirements, and High-Level Data and Communication Needs | Final | 2/7/2013 |
Security
In order to participate in this service package, each physical object should meet or exceed the following security levels.
| Physical Object Security | ||||
|---|---|---|---|---|
| Physical Object | Confidentiality | Integrity | Availability | Security Class |
| Alerting and Advisory System | Moderate | High | Moderate | Class 3 |
| Emergency Management Center | High | High | High | Class 5 |
| Maint and Constr Management Center | High | High | High | Class 5 |
| Other Emergency Management Centers | High | High | High | Class 5 |
| Security Monitoring Equipment | Moderate | Moderate | Moderate | Class 2 |
| Social Media | Moderate | Moderate | Low | Class 2 |
| Surface Transportation Weather Service | Low | Moderate | Moderate | Class 1 |
| Traffic Management Center | High | High | High | Class 5 |
| Transit Management Center | High | High | High | Class 5 |
| Weather Service System | Low | Moderate | Moderate | Class 1 |
In order to participate in this service package, each information flow triple should meet or exceed the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Source | Destination | Information Flow | Confidentiality | Integrity | Availability |
| Basis | Basis | Basis | |||
| Alerting and Advisory System | Emergency Management Center | alerts and advisories | Moderate | High | Moderate |
| Large numbers of alerts and advisories may be supported by this flow, and while much of this information is eventually intended for public release, it could be misinterpreted. Better to keep confidential to the point where it is reformatted and presented in a fashion suitable to widespread distribution. It could include limited PII in incident descriptions, which also justifies obfuscation. | Large numbers of alerts and advisories, if incorrectly reported, could have widespread effects on the management of the surface transportation system. If the scale is small this might be reduced to MODERATE. | Should be reported in timely and consistent fashion to enable proper system management. Failure to receive this flow could lead to significant mobility degradation. | |||
| Alerting and Advisory System | Maint and Constr Management Center | alerts and advisories | Moderate | High | Moderate |
| Large numbers of alerts and advisories may be supported by this flow, and while much of this information is eventually intended for public release, it could be misinterpreted. Better to keep confidential to the point where it is reformatted and presented in a fashion suitable to widespread distribution. It could include limited PII in incident descriptions, which also justifies obfuscation. | Large numbers of alerts and advisories, if incorrectly reported, could have widespread effects on the management of the surface transportation system. If the scale is small this might be reduced to MODERATE. | Should be reported in timely and consistent fashion to enable proper system management. Failure to receive this flow could lead to significant mobility degradation. | |||
| Alerting and Advisory System | Traffic Management Center | alerts and advisories | Moderate | High | Moderate |
| Large numbers of alerts and advisories may be supported by this flow, and while much of this information is eventually intended for public release, it could be misinterpreted. Better to keep confidential to the point where it is reformatted and presented in a fashion suitable to widespread distribution. It could include limited PII in incident descriptions, which also justifies obfuscation. | Large numbers of alerts and advisories, if incorrectly reported, could have widespread effects on the management of the surface transportation system. If the scale is small this might be reduced to MODERATE. | Should be reported in timely and consistent fashion to enable proper system management. Failure to receive this flow could lead to significant mobility degradation. | |||
| Alerting and Advisory System | Transit Management Center | alerts and advisories | Moderate | High | Moderate |
| Large numbers of alerts and advisories may be supported by this flow, and while much of this information is eventually intended for public release, it could be misinterpreted. Better to keep confidential to the point where it is reformatted and presented in a fashion suitable to widespread distribution. It could include limited PII in incident descriptions, which also justifies obfuscation. | Large numbers of alerts and advisories, if incorrectly reported, could have widespread effects on the management of the surface transportation system. If the scale is small this might be reduced to MODERATE. | Should be reported in timely and consistent fashion to enable proper system management. Failure to receive this flow could lead to significant mobility degradation. | |||
| Emergency Management Center | Emergency System Operator | emergency operations status | Moderate | High | High |
| Emergency system controls should not be casually viewable as they impact the availability of emergency services, which if known could be leveraged for illegal activity. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Emergency Management Center | Maint and Constr Management Center | incident information | High | Moderate | Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the EMC should be able to know if the M&CMC has received a message. | |||
| Emergency Management Center | Maint and Constr Management Center | threat information | Moderate | High | High |
| This data is used to determine if there may be a threat to the transportation infrastructure. As this may provoke a response against that threat, this information should be protected from viewing by parties that may be related to the threat. | All threat-related flows should have some measure of confidence assigned to them, as they will necessarily provoke responses from the receiving entities. Corrupted or forged data could inhibit that response or cause one when none is warranted. Both of these cases offer significant negative impacts. Given the scope of the transportation system, we set this HIGH. For small-scoped systems, this may be MODERATE if the response would never be significantly different than daily operations. | Since this information may indicate a threat against the transportation system, including personal safety, we can justify a HIGH rating. Lack of information could lead to extreme consequences if no response is taken. In areas where responses are already part of daily activity, this may be reduced to MODERATE. | |||
| Emergency Management Center | Other Emergency Management Centers | incident report | High | Moderate | Moderate |
| This data contains all information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. DISC: WYO believes this to be MODERATE. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the EMC should be able to know if the TMC has received a message. | |||
| Emergency Management Center | Other Emergency Management Centers | threat information coordination | Moderate | High | High |
| Coordination of threat response would be useful to the source of the threat, and allow them to respond to maximize intent. As such, this information must be kept from them if possible. Given that the EMC is the source of threat response, we justify HIGH. If threat responses in the area are typically similar to day-to-day opeations, can be MODERATE. | All threat-related flows should have some measure of confidence assigned to them, as they will necessarily provoke responses from the receiving entities. Corrupted or forged data could inhibit that response or cause one when none is warranted. Both of these cases offer significant negative impacts. Given the scope of the transportation system, we set this HIGH. For small-scoped systems, this may be MODERATE if the response would never be significantly different than daily operations. | Since this information may indicate a threat against the transportation system, including personal safety, we can justify a HIGH rating. Lack of information could lead to extreme consequences if no response is taken. In areas where responses are already part of daily activity, this may be reduced to MODERATE. | |||
| Emergency Management Center | Security Monitoring Equipment | secure area sensor control | Moderate | High | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: NYC believes this to be low: "This information is directly observable." | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. From NYC: The information sent from TMC directly affect the ITS-RE speed "announcement". | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From NYC: The ITS-RE can work accordingly or in fail-safe if information is not available. | |||
| Emergency Management Center | Security Monitoring Equipment | secure area surveillance control | Moderate | High | Moderate |
| Control flows, even for seemingly innocent devices, should be kept confidential to minimize attack vectors. While an individual installation may not be particularly impacted by a cyberattack of its sensor network, another installation might be severely impacted, and different installations are likely to use similar methods, so compromising one leads to compromising all. DISC: NYC believes this to be low: "This information is directly observable." | Control flows, even for seemingly innocent devices, should have MODERATE integrity at minimum, just to guarantee that intended control messages are received. Incorrect, corrupted, intercepted and modified control messages can or will result in target field devices not behaving according to operator intent. The severity of this depends on the type of device, which is why some devices are set MODERATE and some HIGH. From NYC: The information sent from TMC directly affect the ITS-RE speed "announcement". | Control flow availability is related to the criticality of being able to remotely control the device. For most devices, this is MODERATE. For purely passive devices with no incident relationship, this will be LOW. All devices should have default modes that enable them to operate without backhaul connectivity, so no device warrants a HIGH.. From NYC: The ITS-RE can work accordingly or in fail-safe if information is not available. | |||
| Emergency Management Center | Traffic Management Center | incident information | High | Moderate | Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the EMC should be able to know if the TMC has received a message. | |||
| Emergency Management Center | Traffic Management Center | threat information | Moderate | High | High |
| This data is used to determine if there may be a threat to the transportation infrastructure. As this may provoke a response against that threat, this information should be protected from viewing by parties that may be related to the threat. | All threat-related flows should have some measure of confidence assigned to them, as they will necessarily provoke responses from the receiving entities. Corrupted or forged data could inhibit that response or cause one when none is warranted. Both of these cases offer significant negative impacts. Given the scope of the transportation system, we set this HIGH. For small-scoped systems, this may be MODERATE if the response would never be significantly different than daily operations. | Since this information may indicate a threat against the transportation system, including personal safety, we can justify a HIGH rating. Lack of information could lead to extreme consequences if no response is taken. In areas where responses are already part of daily activity, this may be reduced to MODERATE. | |||
| Emergency Management Center | Transit Management Center | incident information | High | Moderate | Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the EMC should be able to know if the Transit Management Center has received a message. | |||
| Emergency Management Center | Transit Management Center | threat information | Moderate | High | High |
| This data is used to determine if there may be a threat to the transportation infrastructure. As this may provoke a response against that threat, this information should be protected from viewing by parties that may be related to the threat. | All threat-related flows should have some measure of confidence assigned to them, as they will necessarily provoke responses from the receiving entities. Corrupted or forged data could inhibit that response or cause one when none is warranted. Both of these cases offer significant negative impacts. Given the scope of the transportation system, we set this HIGH. For small-scoped systems, this may be MODERATE if the response would never be significantly different than daily operations. | Since this information may indicate a threat against the transportation system, including personal safety, we can justify a HIGH rating. Lack of information could lead to extreme consequences if no response is taken. In areas where responses are already part of daily activity, this may be reduced to MODERATE. | |||
| Emergency System Operator | Emergency Management Center | emergency operations input | Moderate | High | High |
| Emergency system controls should not be casually viewable as they impact the availability of emergency services, which if known could be leveraged for illegal activity. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Maint and Constr Center Personnel | Maint and Constr Management Center | maint and constr center personnel input | High | High | High |
| Direct interactions between personnel and systems in a backoffice environment are effectively protected by physical means, so long as the interaction is in a dedicated facility. If this interaction is virtual (i.e. ,the MCMC is not directly in front of the MCMC Personnel, like in a cloud-based system) then the user's input requires some degree of obfuscation depending on sensitivity of information. Given that this could include information about compromised or ineffectual systems, including security systems, the potential for damage is high. Thus, HIGH. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Maint and Constr Management Center | Emergency Management Center | incident information | High | Moderate | Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the MCMC should be able to know if the EMC has received a message. | |||
| Maint and Constr Management Center | Maint and Constr Center Personnel | maint and constr operations information presentation | Not Applicable | Moderate | Moderate |
| System maintenance flows should have some protection from casual viewing, as otherwise imposters could gain illicit control over field equipment | Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. | The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. | |||
| Other Emergency Management Centers | Emergency Management Center | incident report | High | Moderate | Moderate |
| This data contains all information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. DISC: WYO believes this to be MODERATE. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the EMC should be able to know if the TMC has received a message. | |||
| Other Emergency Management Centers | Emergency Management Center | threat information coordination | Moderate | High | High |
| Coordination of threat response would be useful to the source of the threat, and allow them to respond to maximize intent. As such, this information must be kept from them if possible. Given that the EMC is the source of threat response, we justify HIGH. If threat responses in the area are typically similar to day-to-day opeations, can be MODERATE. | All threat-related flows should have some measure of confidence assigned to them, as they will necessarily provoke responses from the receiving entities. Corrupted or forged data could inhibit that response or cause one when none is warranted. Both of these cases offer significant negative impacts. Given the scope of the transportation system, we set this HIGH. For small-scoped systems, this may be MODERATE if the response would never be significantly different than daily operations. | Since this information may indicate a threat against the transportation system, including personal safety, we can justify a HIGH rating. Lack of information could lead to extreme consequences if no response is taken. In areas where responses are already part of daily activity, this may be reduced to MODERATE. | |||
| Security Monitoring Equipment | Emergency Management Center | secure area sensor data | Moderate | Moderate | Moderate |
| Any security or surveillance data should be protected from casual viewing. An attacker could use this information to assess a facility's susceptibility to attack, or intercept it and use it to monitor their own progress. | Security and surveillance data needs guarantee of accuracy. However, there will be procedures in place to verify any alarms or alerts, suggesting this could be MODERATE in most instances. For sensitive areas, this might be HIGH. | Surveillance and security data should be generally available to security systems; if this goes down it could indicate some kind of hostile action against the monitored facility. This might be HIGH for areas that are sensitive or have particularly high value equipment. | |||
| Security Monitoring Equipment | Emergency Management Center | secure area surveillance data | Moderate | Moderate | Moderate |
| Any security or surveillance data should be protected from casual viewing. An attacker could use this information to assess a facility's susceptibility to attack, or intercept it and use it to monitor their own progress. | Security and surveillance data needs guarantee of accuracy. However, there will be procedures in place to verify any alarms or alerts, suggesting this could be MODERATE in most instances. For sensitive areas, this might be HIGH. | Surveillance and security data should be generally available to security systems; if this goes down it could indicate some kind of hostile action against the monitored facility. This might be HIGH for areas that are sensitive or have particularly high value equipment. | |||
| Social Media | Emergency Management Center | traveler sourced updates | Moderate | Moderate | Low |
| This is likely to include the traveler location and may include traveler identity as well. This PII could be used by an attacker to the detriment of the traveler. | If this information is not correct the end user of the social media will likely find othe avenues for obtaining this information. | If this interface is not available the traveler will likely find other means to acquire the necessary information. | |||
| Surface Transportation Weather Service | Emergency Management Center | transportation weather information | Low | Moderate | Moderate |
| Typically intended for public distribution. | While there are many sources of weather information, some guarantee of correctness is justifiable to keep confidence in provided service. In areas with severe weather it may be justifiable to raise this to HIGH. | There should be other sources of this data. It does need to be reliable however; weather can change quickly, and depending on the destination and its operational strategies, timely response may be important. In areas with severe weather it may be justifiable to raise this to HIGH. | |||
| Traffic Management Center | Emergency Management Center | incident information | High | Moderate | Moderate |
| This data contains all of the information regarding the incident. This could include personal information regarding persons involved in the incident. It could also include sensitive information regarding special events or closures. | Minor discrepancies in this data should not have a catastrophic effect, but it should be reasonably controlled and accurate. | A few missed messages should not have a significant effect. However, most messages should make it through and the TMC should be able to know if the EMC has received a message. | |||
| Traffic Management Center | Traffic Operations Personnel | traffic operator data | Moderate | Moderate | Moderate |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Information presented to backoffice system operators must be consistent or the operator may perform actions that are not appropriate to the real situation. | The backoffice system operator should have access to system operation. If this interface is down then control is effectively lost, as without feedback from the system the operator has no way of knowing what is the correct action to take. | |||
| Traffic Operations Personnel | Traffic Management Center | traffic operator input | Moderate | High | High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Transit Management Center | Emergency Management Center | transit emergency data | Moderate | High | High |
| Security event or other emergency could be used by an attacker to confirm or further a crime in progress. | This must be accurate to ensure correct response, as human safety may be at stake. | Human safety could be at stake, which suggest sever consequences. | |||
| Transit Management Center | Transit Operations Personnel | transit operations status | Moderate | High | High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Transit Operations Personnel | Transit Management Center | transit operations personnel input | Moderate | High | High |
| Backoffice operations flows should have minimal protection from casual viewing, as otherwise imposters could gain illicit control or information that should not be generally available. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | Backoffice operations flows should generally be correct and available as these are the primary interface between operators and system. | |||
| Weather Service System | Emergency Management Center | weather information | Low | Moderate | Moderate |
| Typically intended for public distribution. | While there are many sources of weather information, some guarantee of correctness is justifiable to keep confidence in provided service. Even for areas with significant weather events that drive emergency activities, it would be difficult to justify HIGH for this flow. While the repurcussions of inaccurate data may be significant, they are probably not catastrophic. | The Emergency Management Center relies on weather data for planning and decision making, so this flow needs to be reliable. In areas with flash-weather issues, this might be HIGH. | |||
Standards
The following table lists the standards associated with physical objects in this service package. For standards related to interfaces, see the specific information flow triple pages. These pages can be accessed directly from the SVG diagram(s) located on the Physical tab, by clicking on each information flow line on the diagram.
| Name | Title | Physical Object |
|---|---|---|
| NEMA TS 8 Cyber and Physical Security | Cyber and Physical Security for Intelligent Transportation Systems | Traffic Management Center |
System Requirements
| System Requirement | Need | ||
|---|---|---|---|
| 001 | The system shall monitor information from Alerting and Advisory Systems such as the Information Sharing and Analysis Centers (ISACs), the National Infrastructure Protection Center (NIPC), the Homeland Security Advisory System (HSAS), etc. The information may include assessments (general incident and vulnerability awareness information), advisories (identification of threats or recommendations to increase preparedness levels), or alerts (information on imminent or in-progress emergencies). | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 002 | The system shall receive incident information from other transportation management centers to support the early warning system. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 003 | The system shall support the entry of alert and advisory information directly from the emergency system operator. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 004 | The system shall receive potential incident information from social media sources to support the early warning system. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 005 | The system shall provide the capability to correlate alerts and advisories, incident information, and security sensor and surveillance data. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 006 | The system shall broadcast wide-area alerts and advisories to traffic management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 007 | The system shall broadcast wide-area alerts and advisories to transit management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 008 | The system shall broadcast wide-area alerts and advisories to maintenance centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 009 | The system shall broadcast wide-area alerts and advisories to other emergency management centers for emergency situations such as severe weather events, civil emergencies, child abduction (AMBER alert system), military activities, and other situations that pose a threat to life and property. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 010 | The system shall process status information from each of the centers that have been sent the wide-area alert. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 011 | The system shall coordinate the broadcast of wide-area alerts and advisories with other emergency management centers. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 012 | The system shall present the alert and advisory information and the status of the actions taken in response to the alert by the other centers to the emergency system operator as received from other system inputs. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 013 | The system shall collect current and forecast road and weather information from weather service providers (such as the National Weather Service and value-added sector specific meteorological services). | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 014 | The system shall assimilate current and forecast road conditions and surface weather information to support incident management. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 015 | The system shall provide the road and weather warning and advisories to the emergency responders. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 016 | The system shall remotely monitor and control security sensor data collected in secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). The types of security sensor data include environmental threat (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), infrastructure condition and integrity, intrusion and motion, and object detection sensors. The data may be raw or pre-processed in the field. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 017 | The system shall remotely monitor and control security sensor data collected in traveler secure areas, which include transit stations, transit stops, rest areas, park and ride lots, and other fixed sites along travel routes (e.g., emergency pull-off areas and travel information centers). The types of security sensor data include environmental threat (e.g. chemical agent, toxic industrial chemical, biological, explosives, and radiological sensors), intrusion and motion, and object detection sensors. The data may be raw or pre-processed in the field. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 018 | The system shall identify potential security threats based on collected security sensor data. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 019 | The system shall verify potential security threats by correlating security sensor data from multiple sources. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 020 | The system shall perform threat analysis based on correlations of security sensor and surveillance data. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 021 | The system shall exchange threat analysis data with Alerting and Advisory Systems and use that data in local threat analysis processing. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 022 | The system shall disseminate threat information to other agencies, including traffic, transit, maintenance, rail operations, and other emergency management centers. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 023 | The system shall identify potential security threats based on collected security surveillance data. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 024 | The system shall verify potential security threats by correlating security surveillance data from multiple sources. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 025 | The system shall exchange alert information and status with emergency management centers. The information includes notification of a major emergency such as a natural or man-made disaster, civil emergency, or child abduction. The information may include the alert originator, the nature of the emergency, the geographic area affected by the emergency, the effective time period, etc. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 026 | The system shall receive inputs from the Alerting and Advisory System concerning the possibility or occurrence of severe weather, terrorist activity, or other major emergency, including information provided by the Emergency Alert System. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 027 | The system shall exchange incident and threat information with emergency management centers as well as maintenance and construction centers; including notification of existence of incident and expected severity, location, time and nature of incident. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 028 | The system shall receive information pertaining to a wide-area alert such as weather alerts, disaster situations, or child abductions. This information may come from Emergency Management or from other Alerting and Advisory Systems. | 02 | Emergency Management needs to be able to alert all relevant agencies of detected emergencies. |
| 029 | The system shall coordinate the response to security incidents involving transit with other agencies including Emergency Management, other transit agencies, media, traffic management, and traveler information service providers. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 030 | The system shall include security sensors that monitor conditions of secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 031 | The system shall be remotely controlled by a center. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 032 | The system shall include motion and intrusion detection sensors. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 033 | The system shall remotely process security sensor data and provide an indication of potential incidents or threats to a center. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 034 | The system shall include video and/or audio surveillance of secure areas including facilities (e.g. transit yards) and transportation infrastructure (e.g. bridges, tunnels, interchanges, roadway infrastructure, and transit railways or guideways). | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 035 | The system shall provide raw video or audio data. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |
| 036 | The system shall remotely process video and audio data and provide an indication of potential incidents or threats to a center. | 01 | Emergency Management needs to be able to collect potential threats, alerts, and advisories from various ITS systems to identify emergencies. |